6.5 Flash Cards -Domain 5 - Security Operations
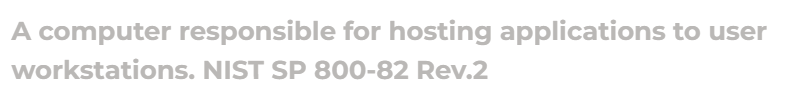
Application Server
Asymmetric Encryption

Checksum

Ciphertext

Classification

Configuration management

Cryptanalyst

Cryptography

Data Loss Prevention (DLP)

Decryption

Degaussing

Digital Signature

Egress Monitoring

Encryption

Encryption System

Hardening

Hash Function

Hashing
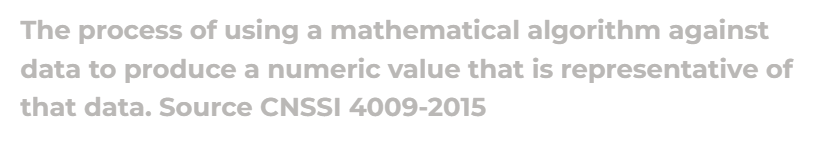
Information Sharing

Ingress Monitoring

Message Digest

Operating System

Patch

Patch Management

Plaintext

Records

Records Retention

Remanence

Request for change (RFC)

Security Governance

Social Engineering

Symmetric Encryption

Web Server

Whaling Attack
