6.3 Flash Cards -Domain 3 - Access Control Concepts
Audit

Crime Prevention Through Environmental Design (CPTED)

Defense in Depth

Discretionary Access Control (DAC)

Encrypt

Firewalls

Insider Threat

iOS

Layered Defense

Linux

Log Anomaly

Logging

Logical Access Control System

Mandatory Access Control

Mantrap

Object

Physical Access Controls

Principle of Least Privilege

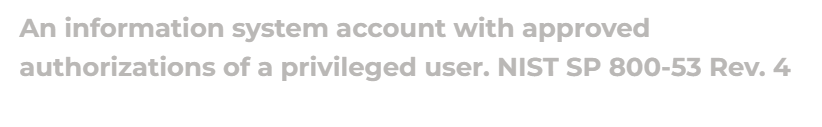
Privileged Account
Ransomware

Role-Based Access Control (RBAC)

Rule

Segregation of Duties

Subject

Technical Controls

Turnstile

Unix

User Provisioning
