6.1 Flash Cards - Domain 1 - Security Principles
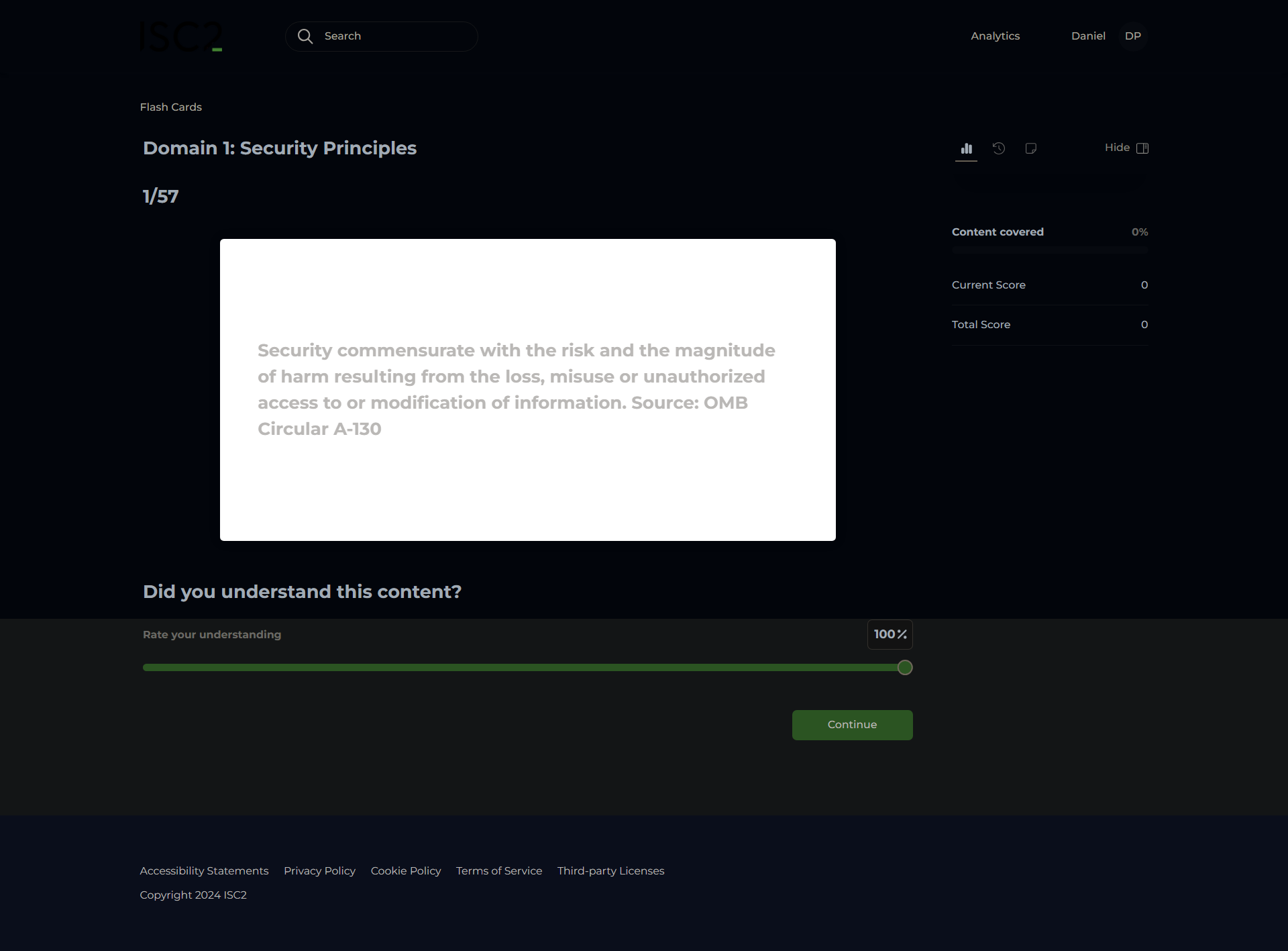
Adequate Security
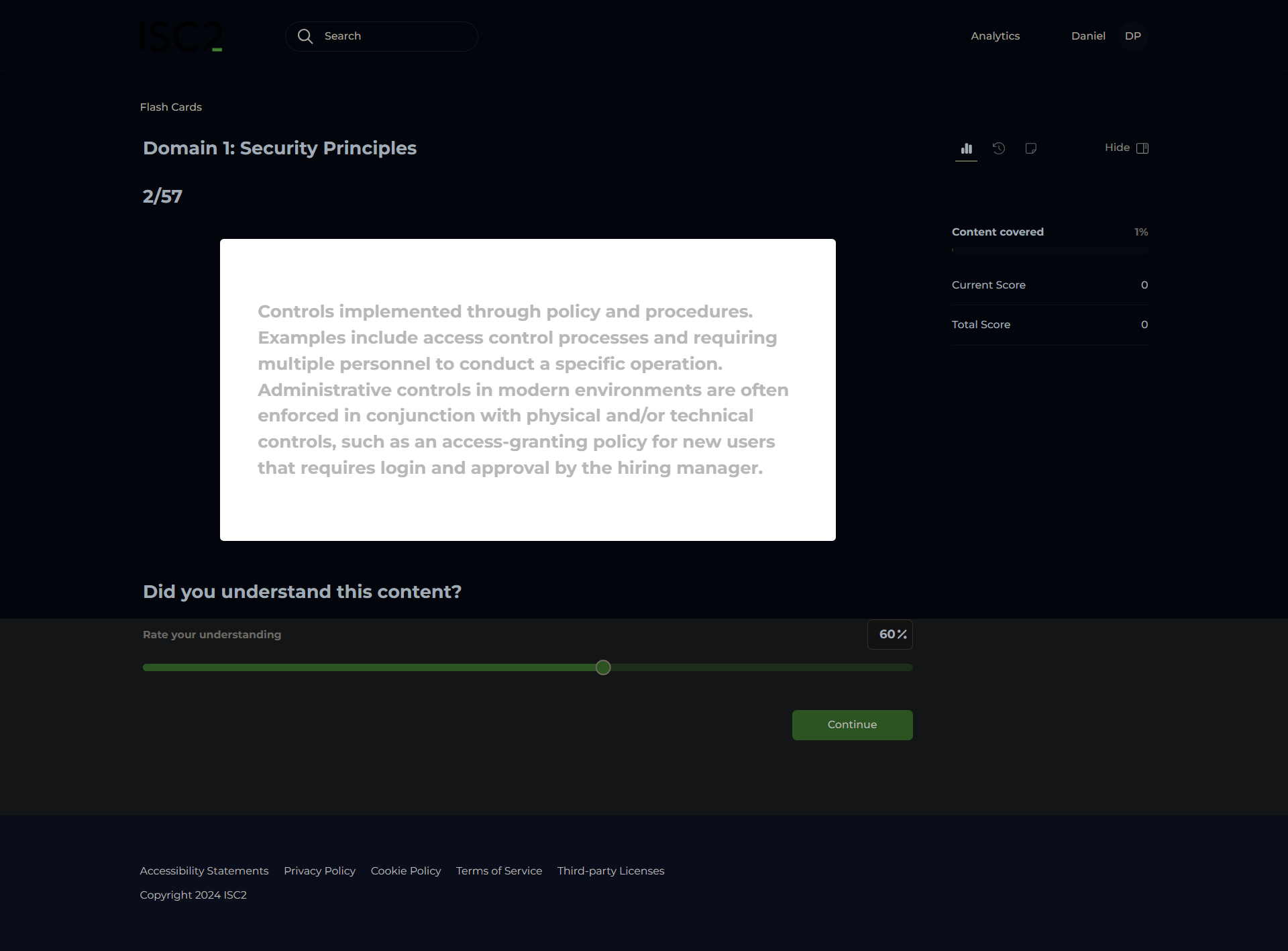
Administrative Controls
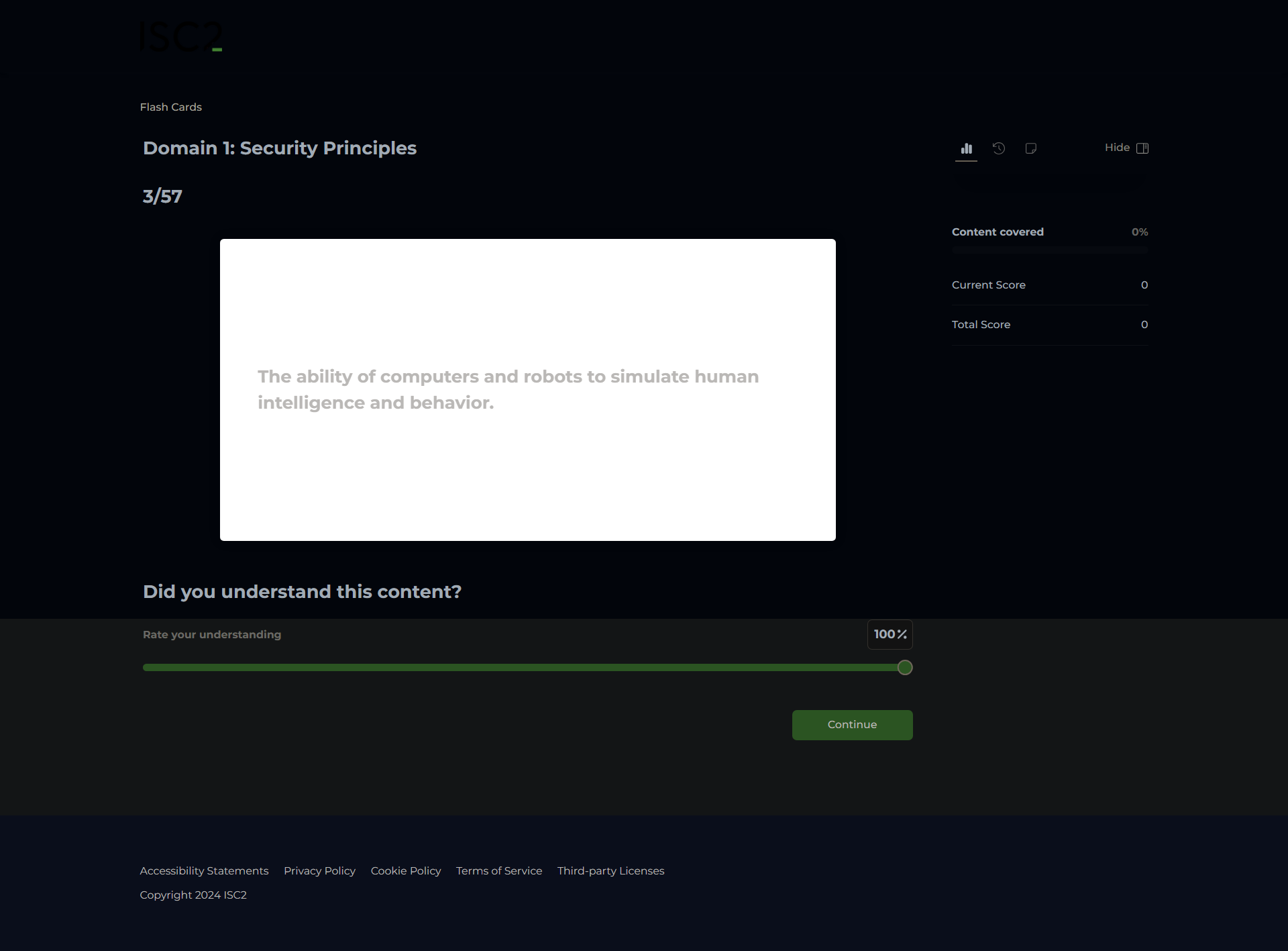
Artificial Intelligence
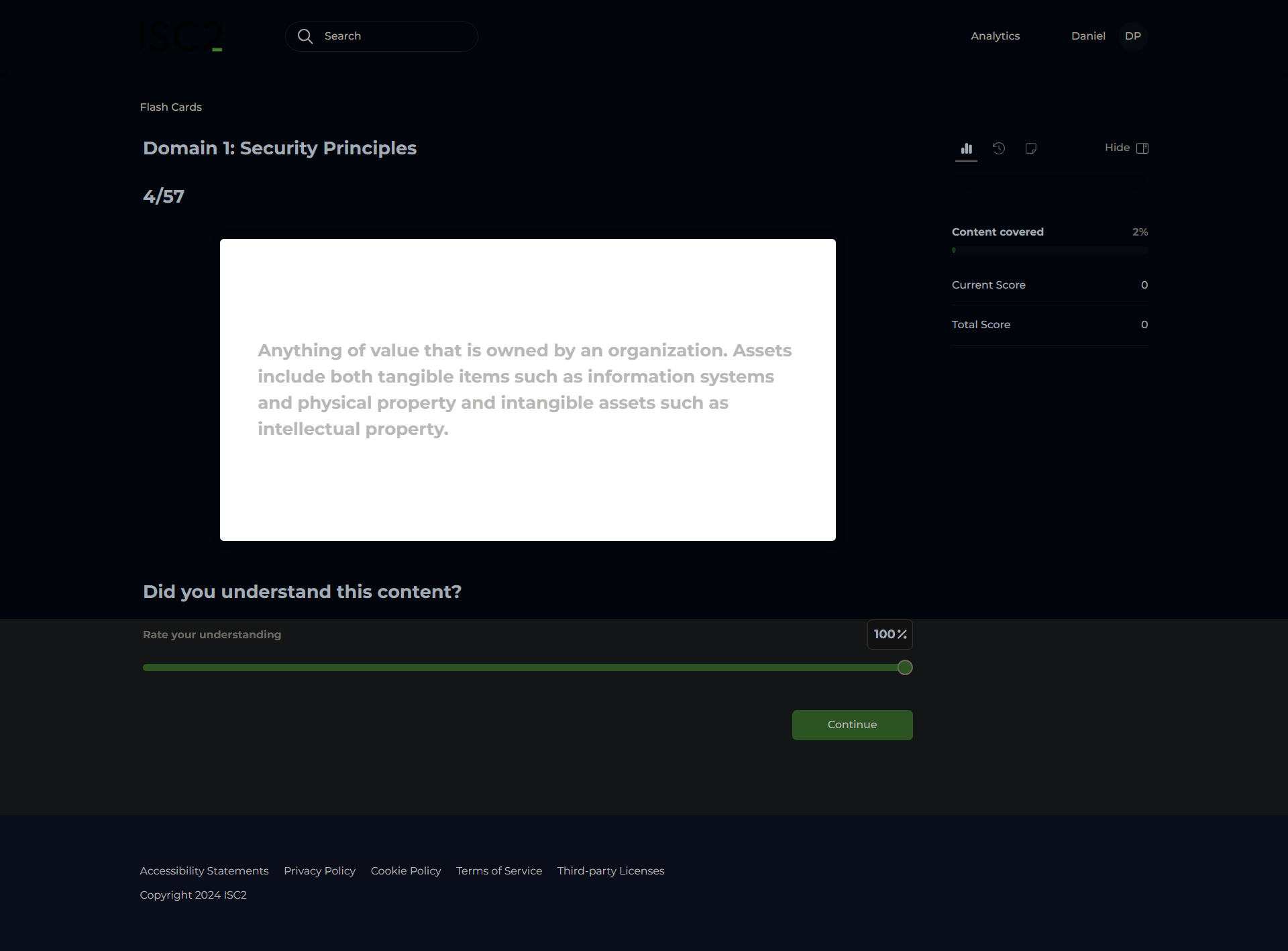
Asset
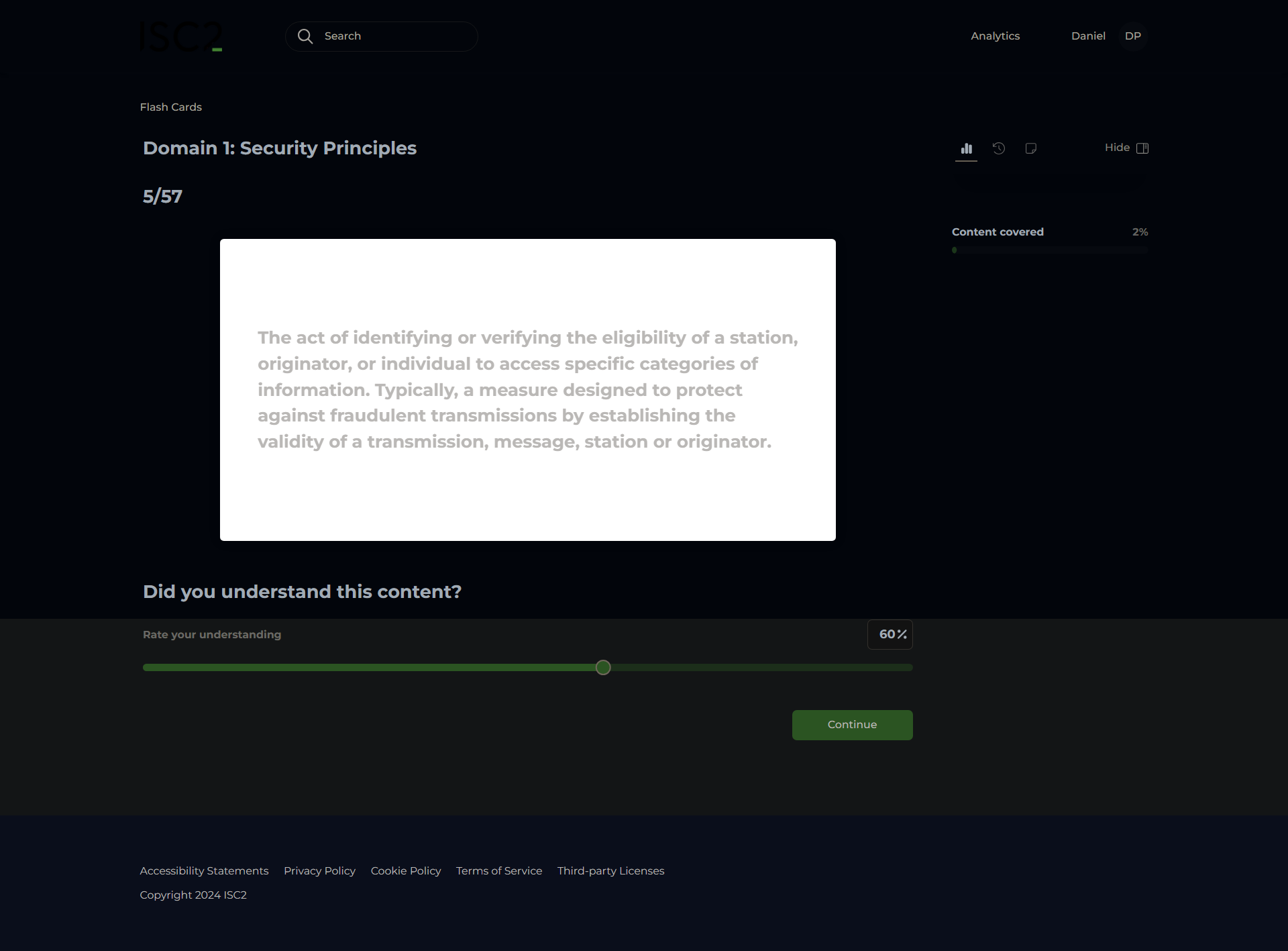
Authentication
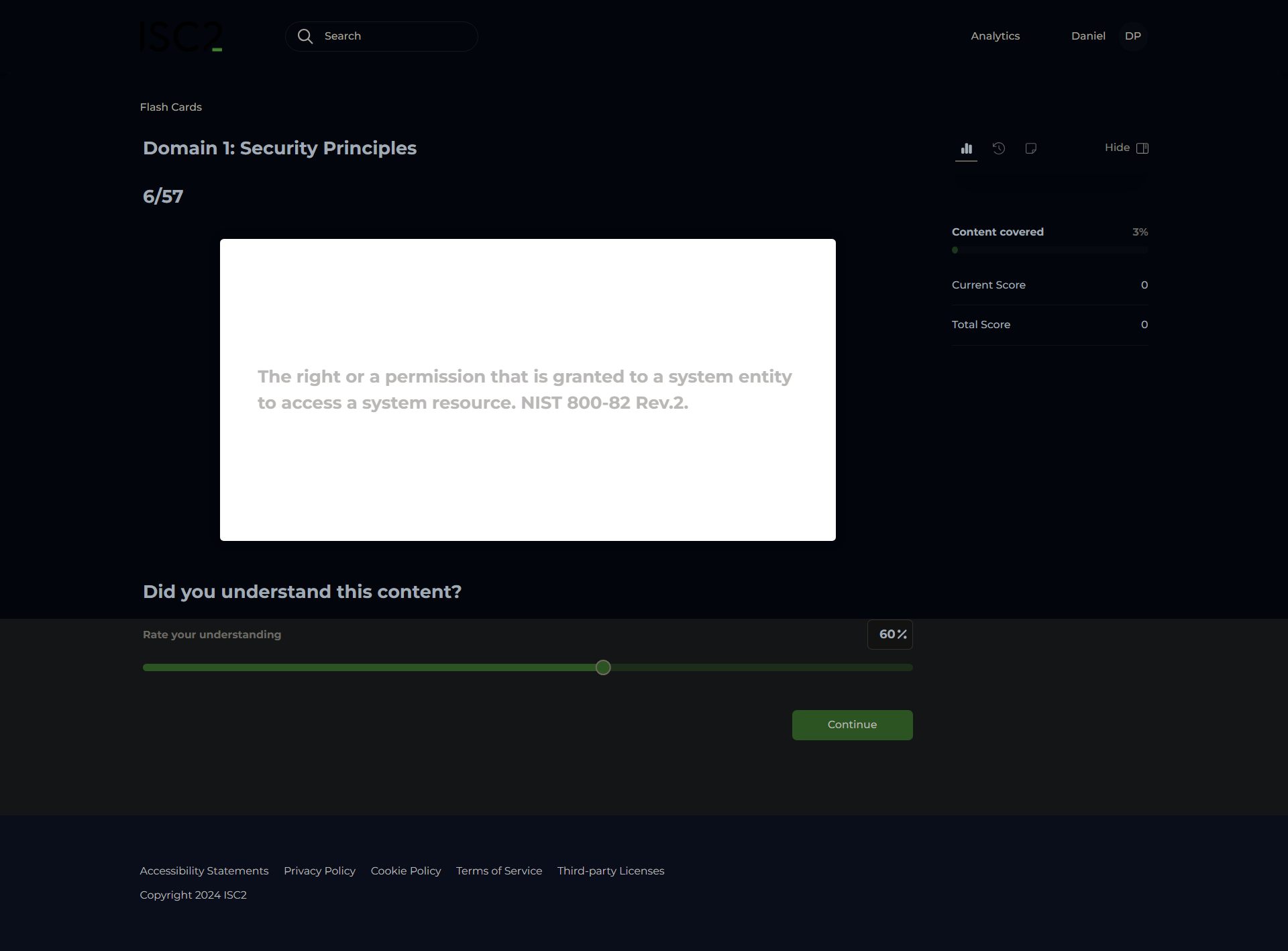
Authorization
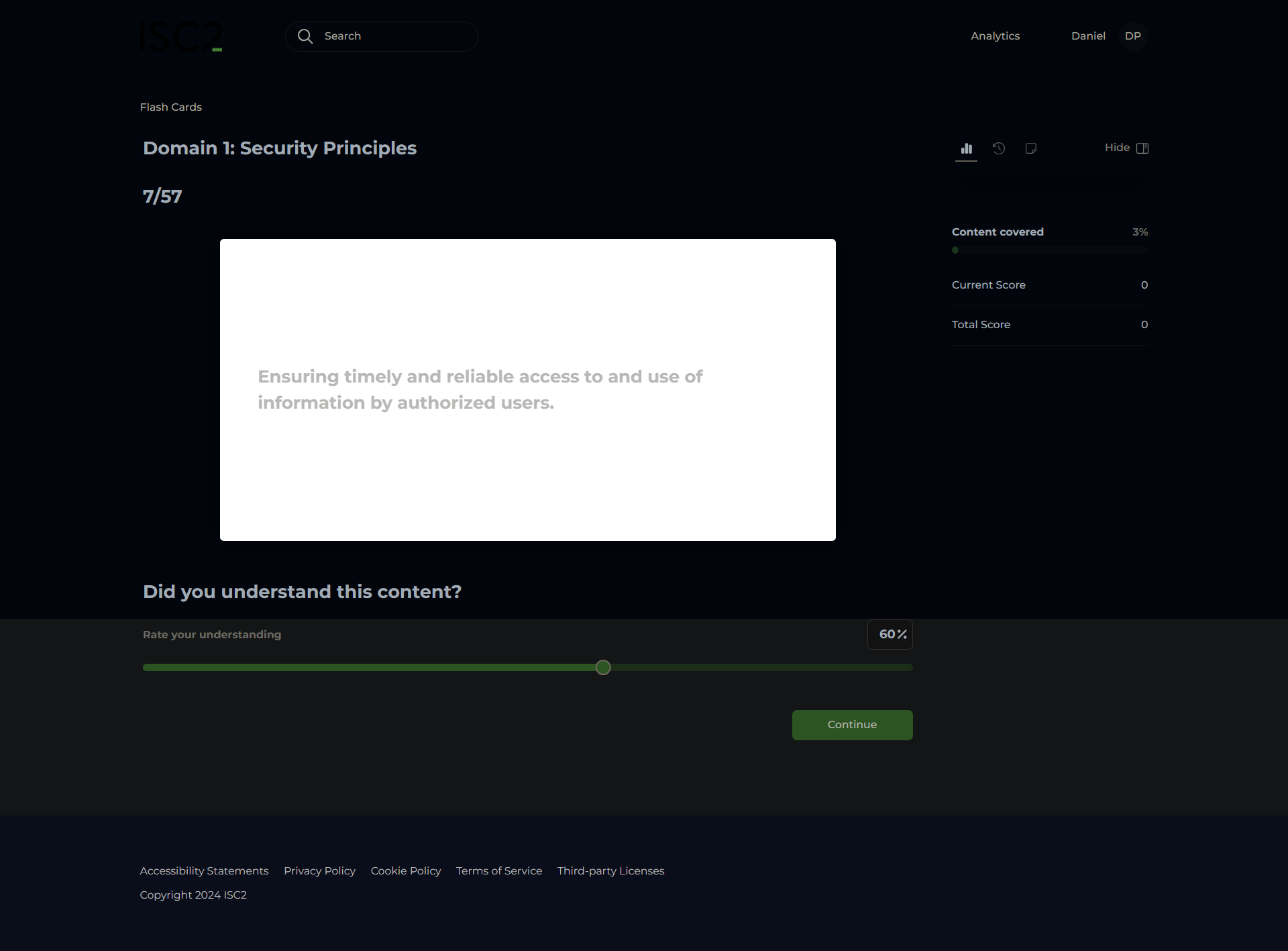
Availability
Baseline
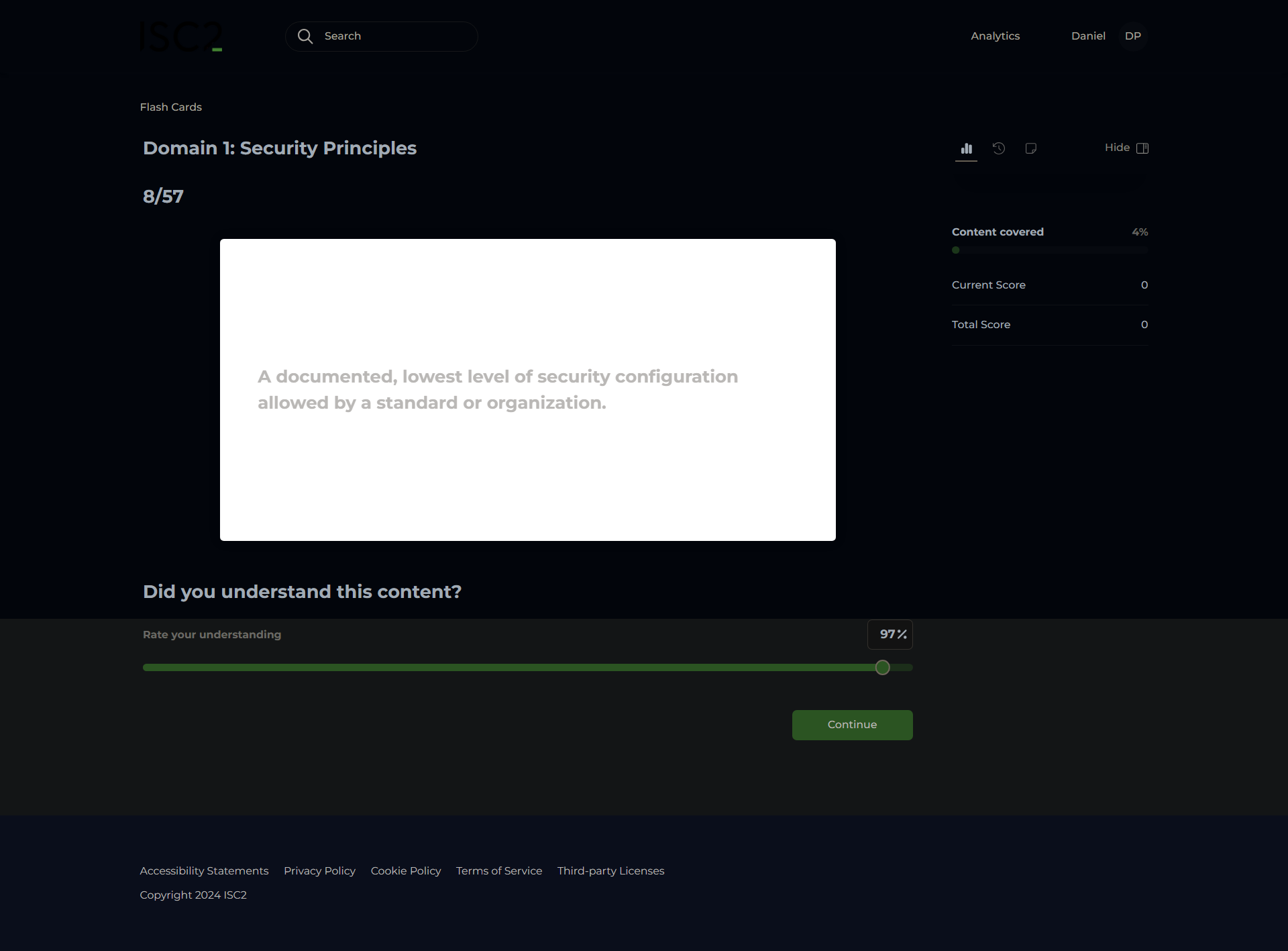
Biometric
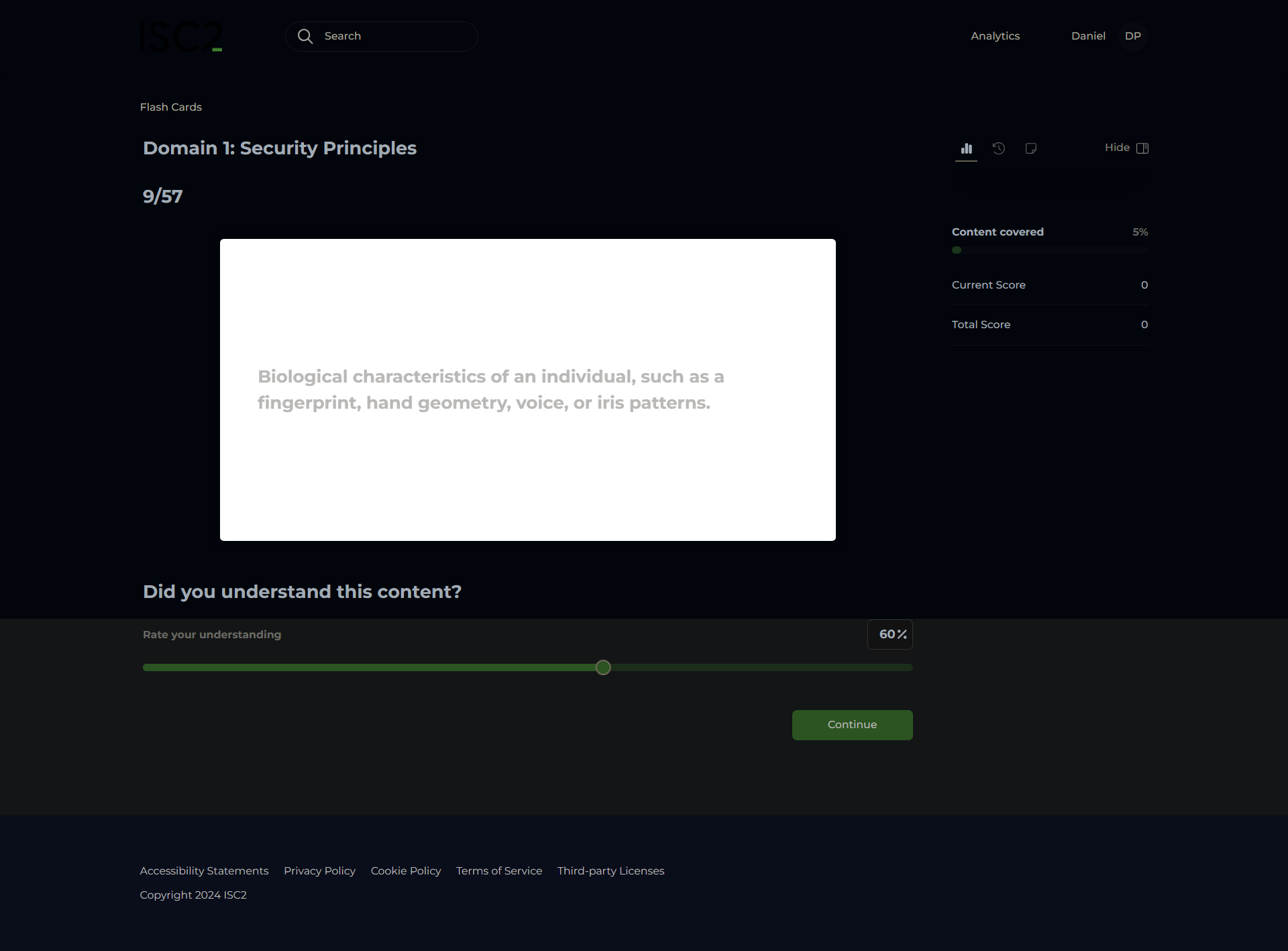
Bot
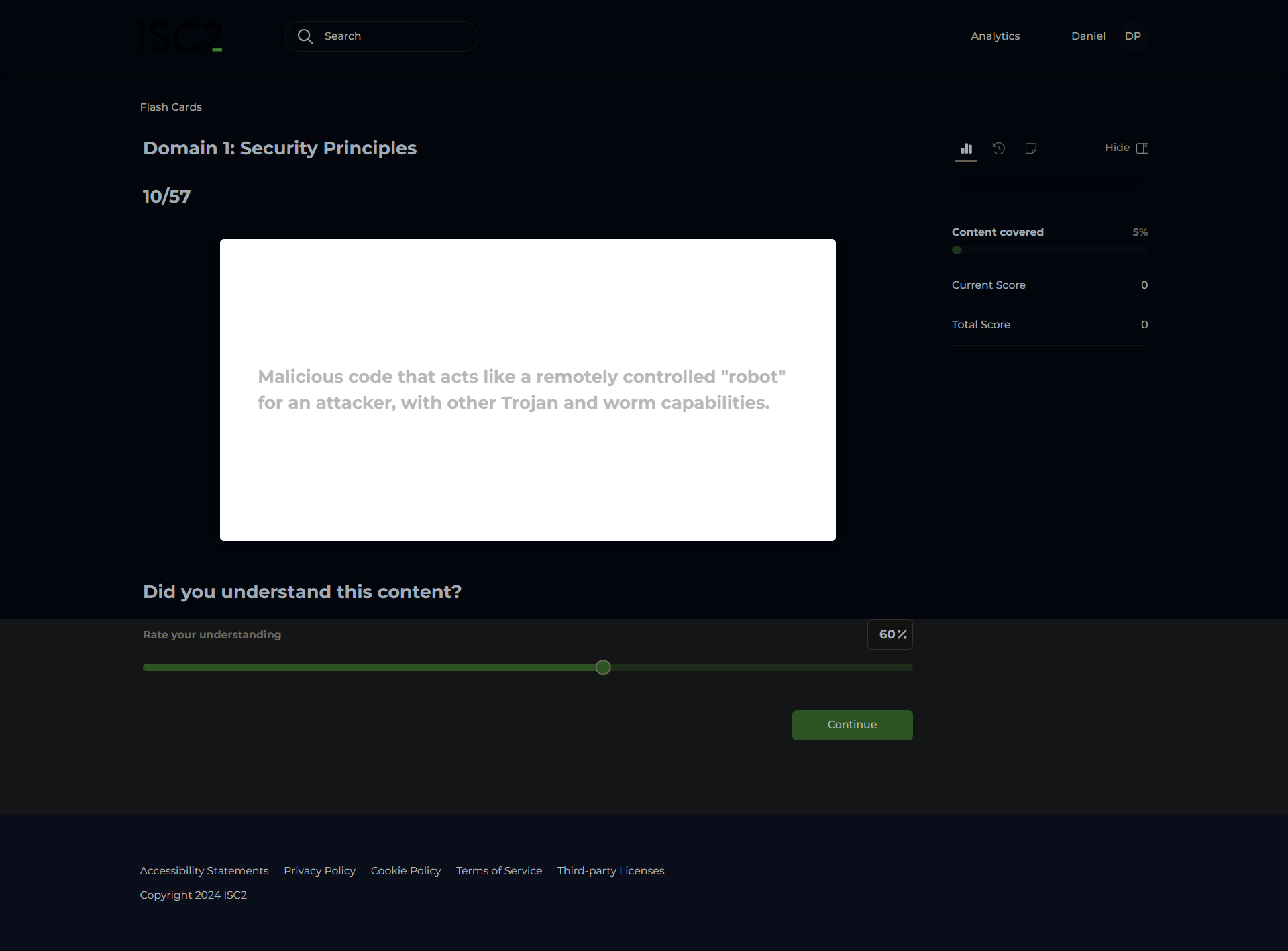
Classified or Sensitive Info
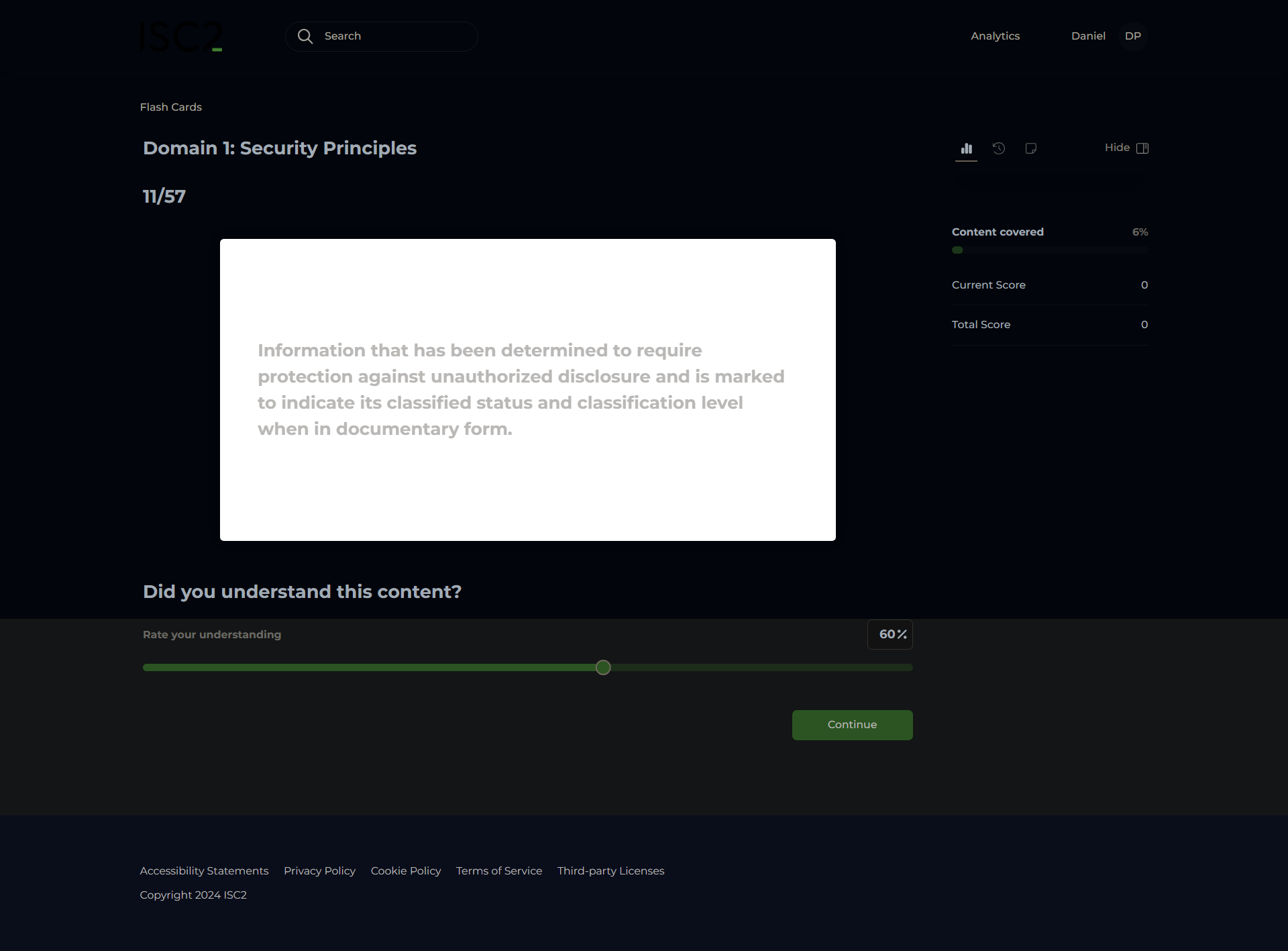
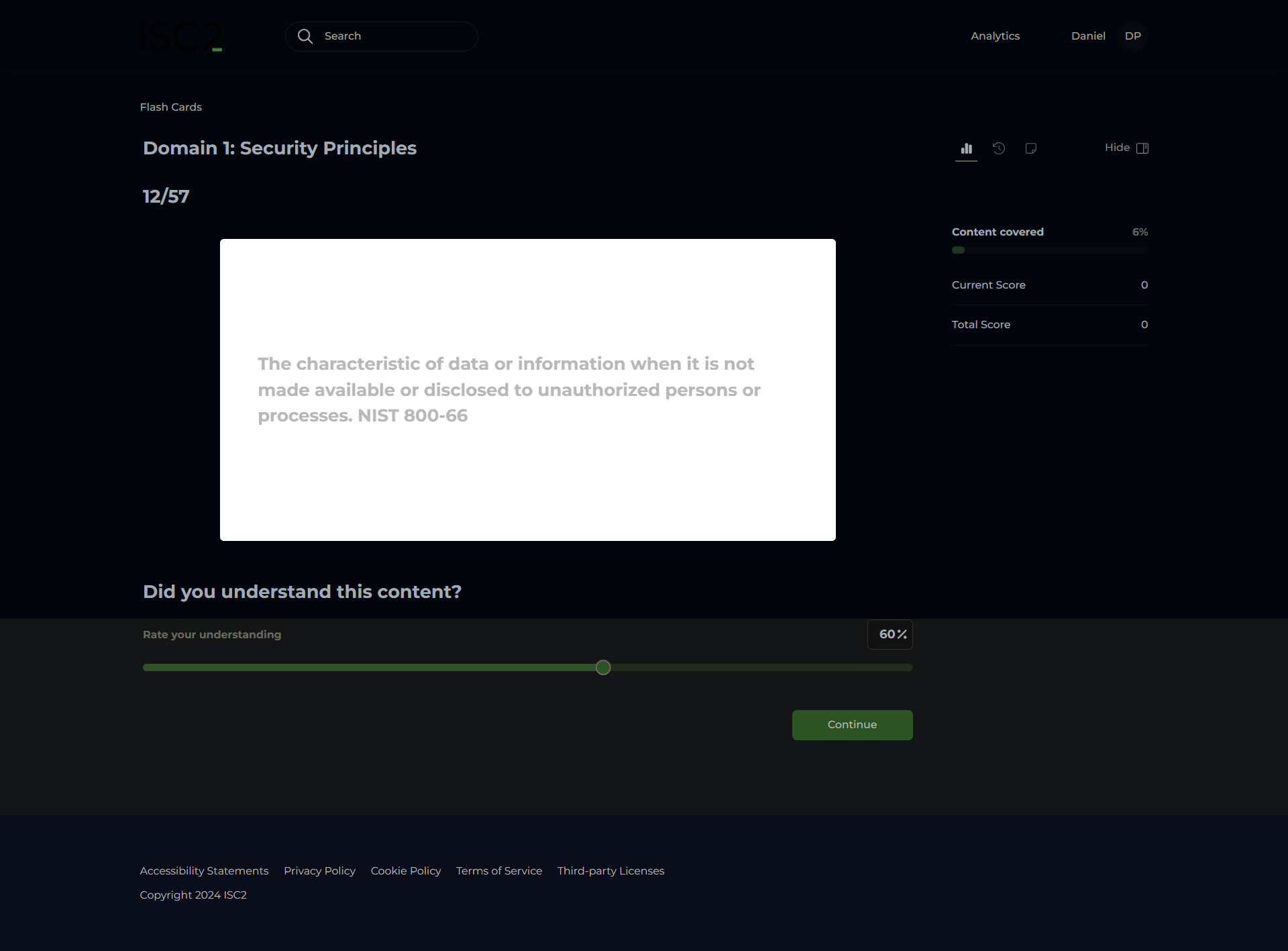
Confidentiality
Criticality
Data Integrity
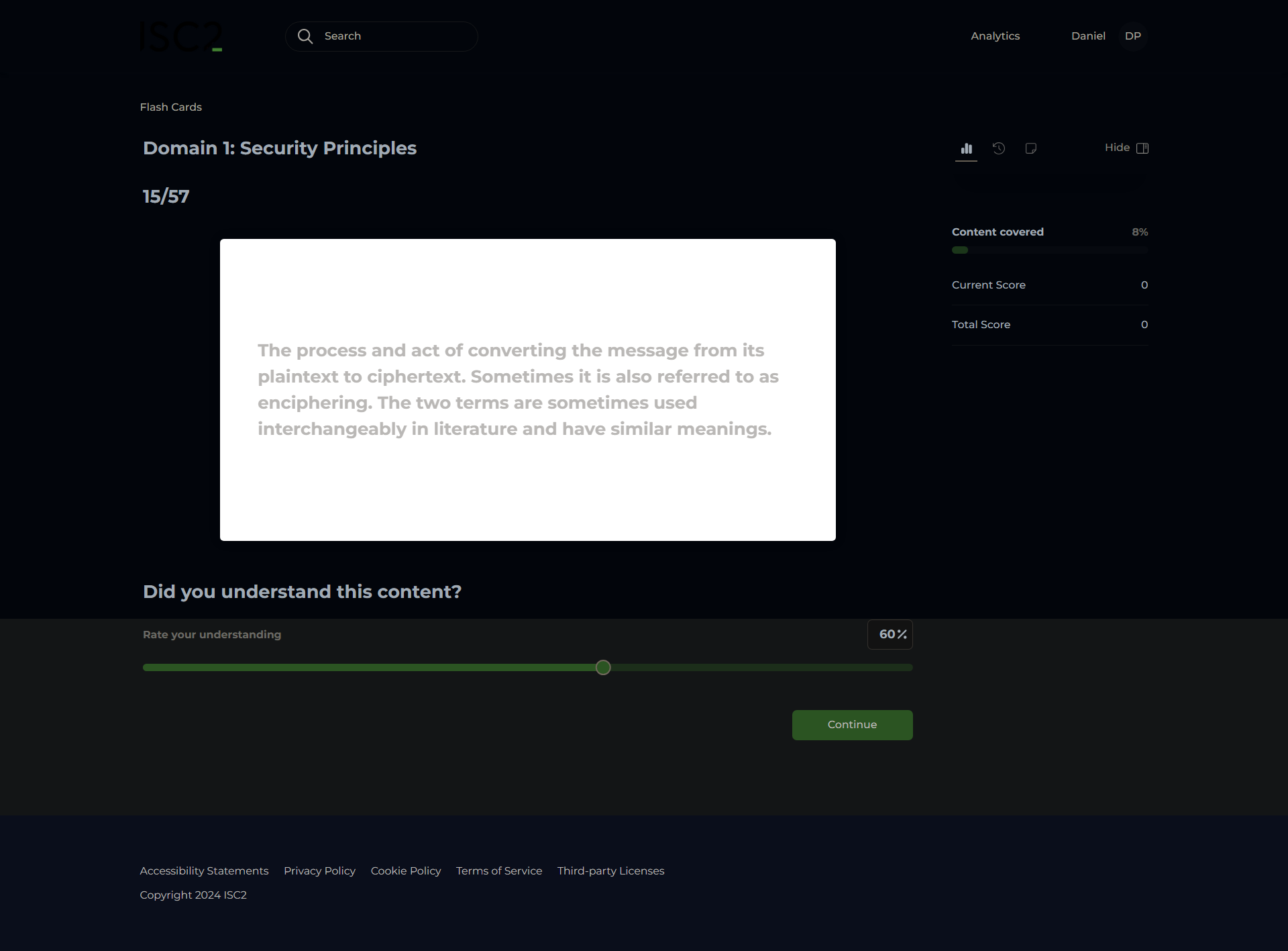
Encryption
General Data Protection Regulation (GDPR)
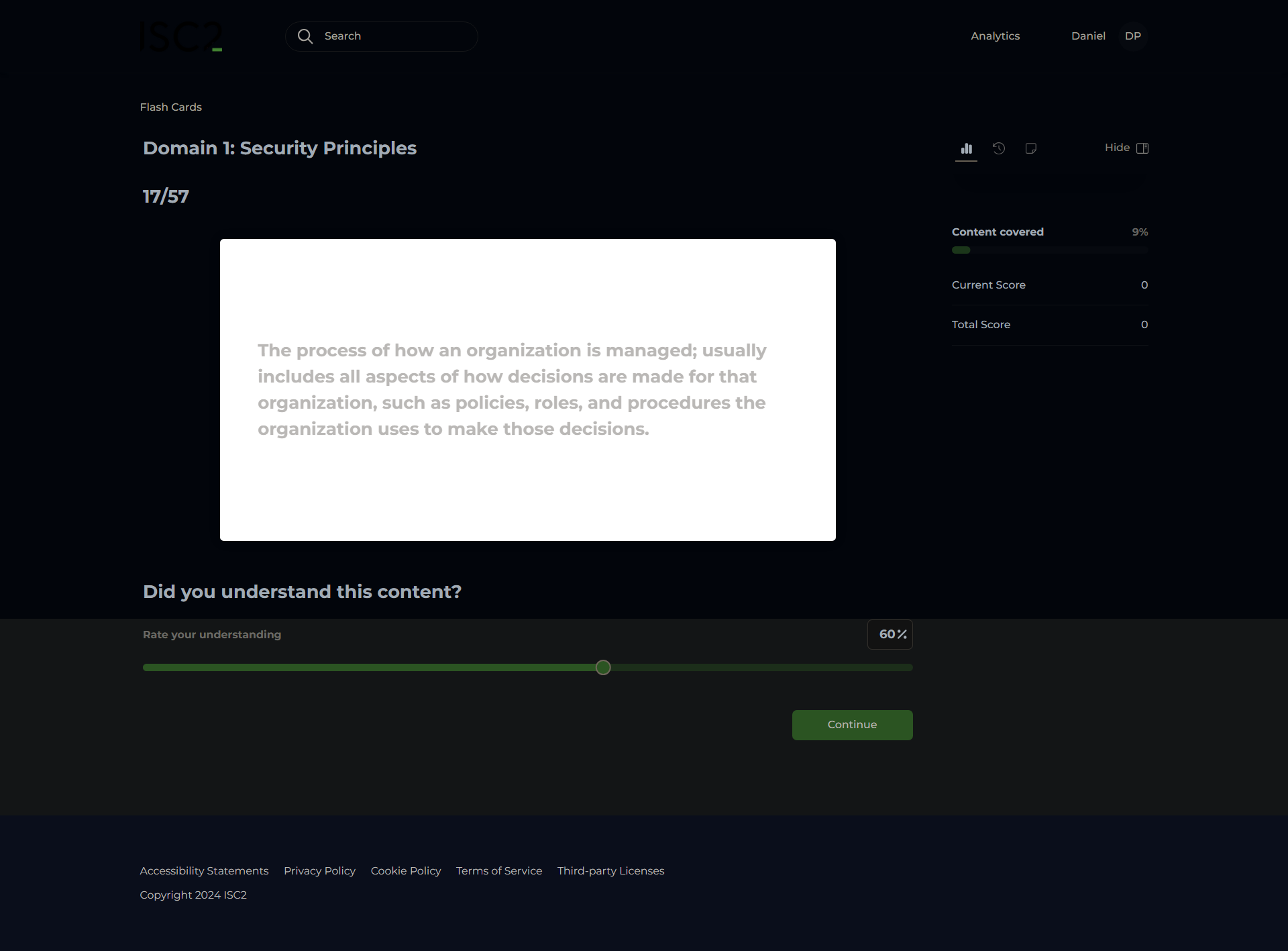
Governance
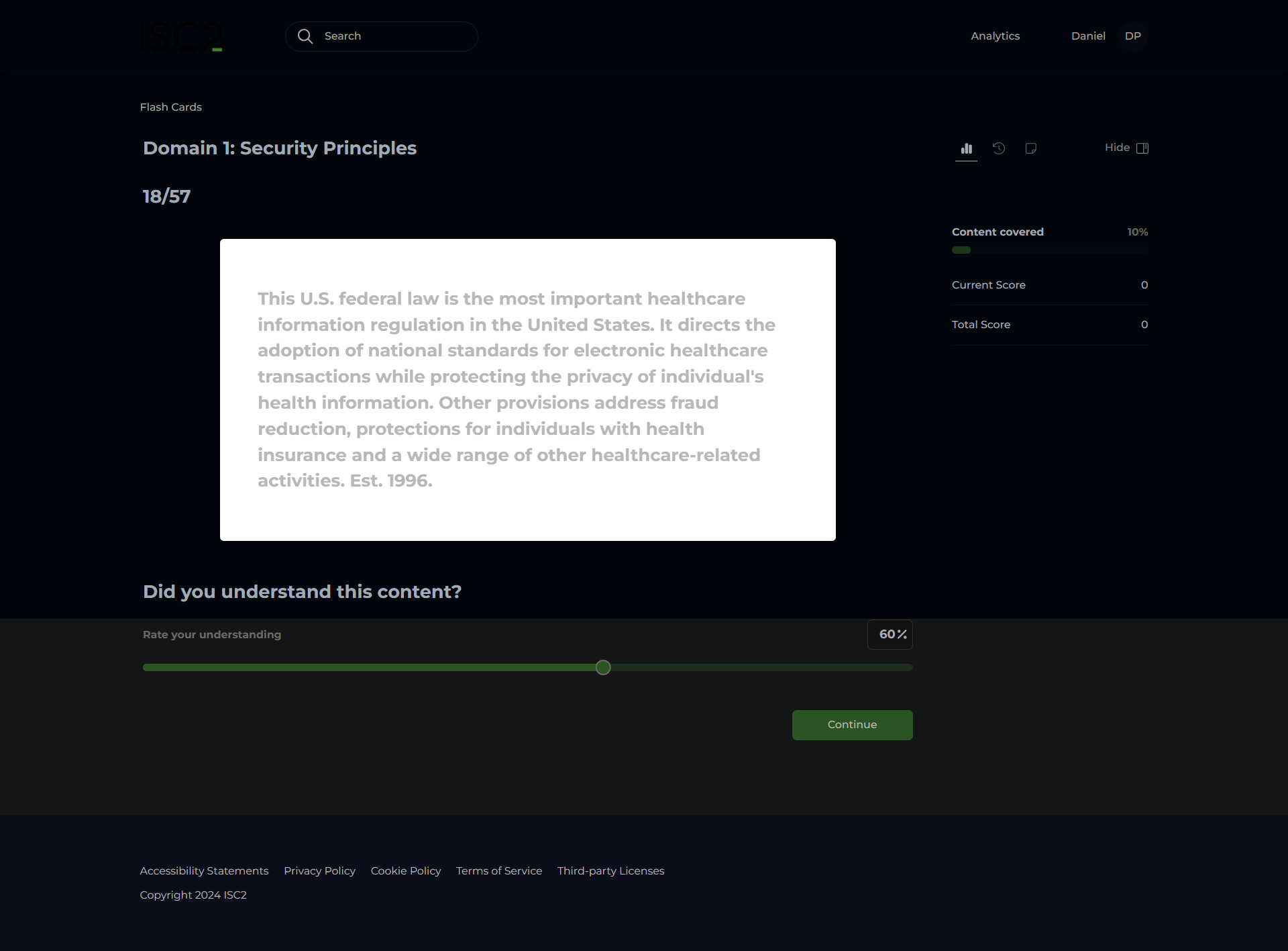
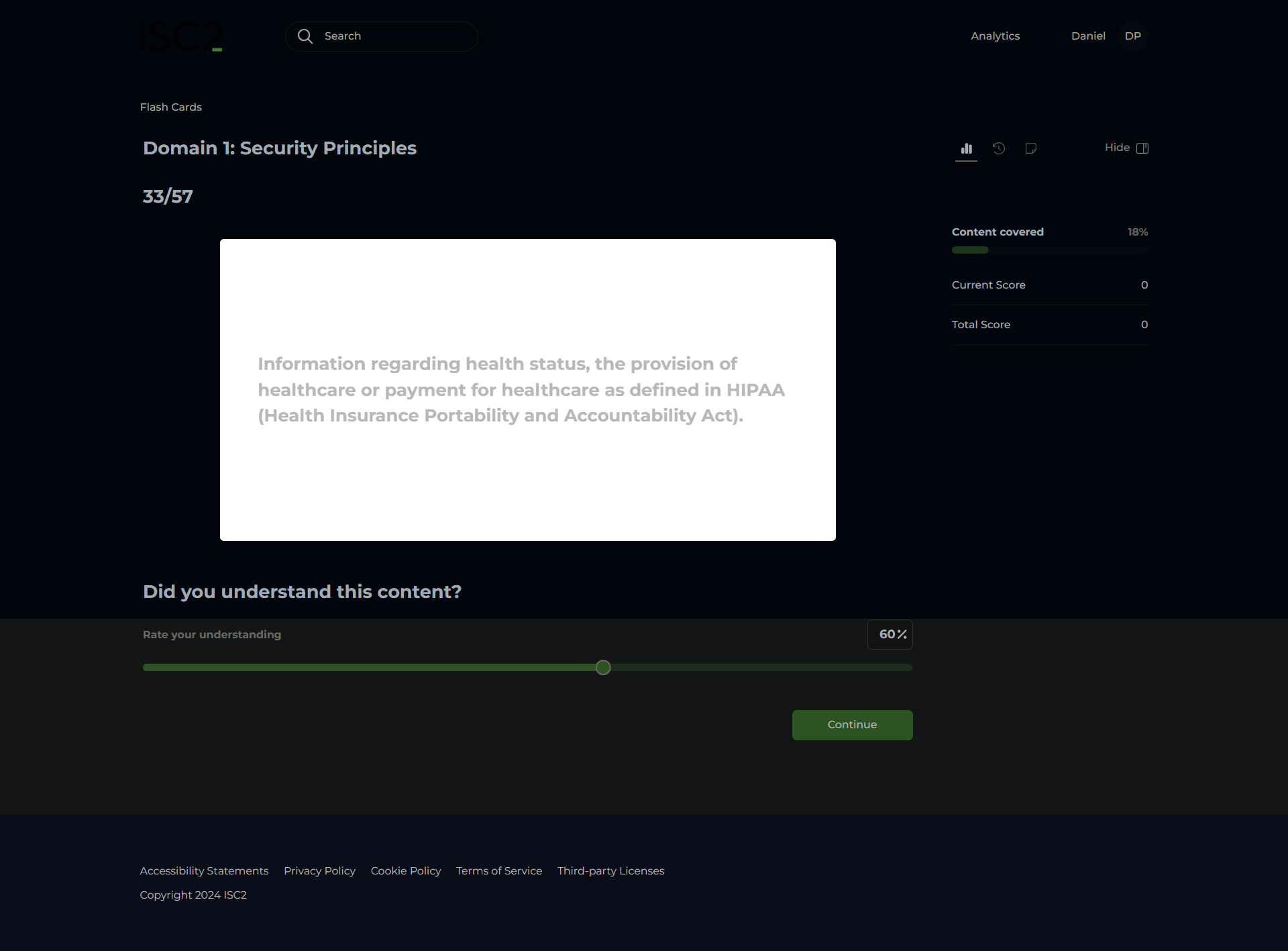
Health Insurance Portability and Accountability Act (HIPAA)
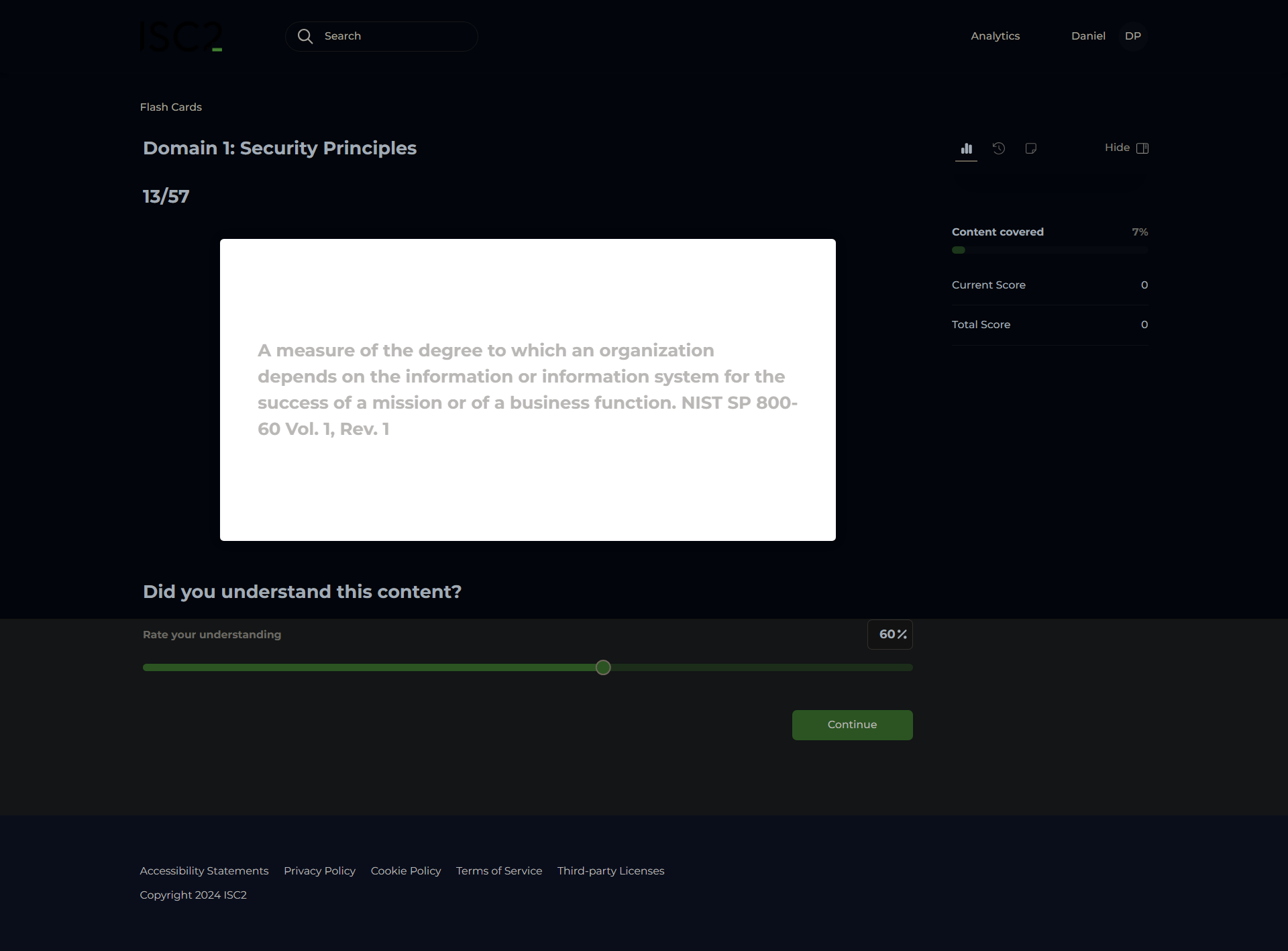
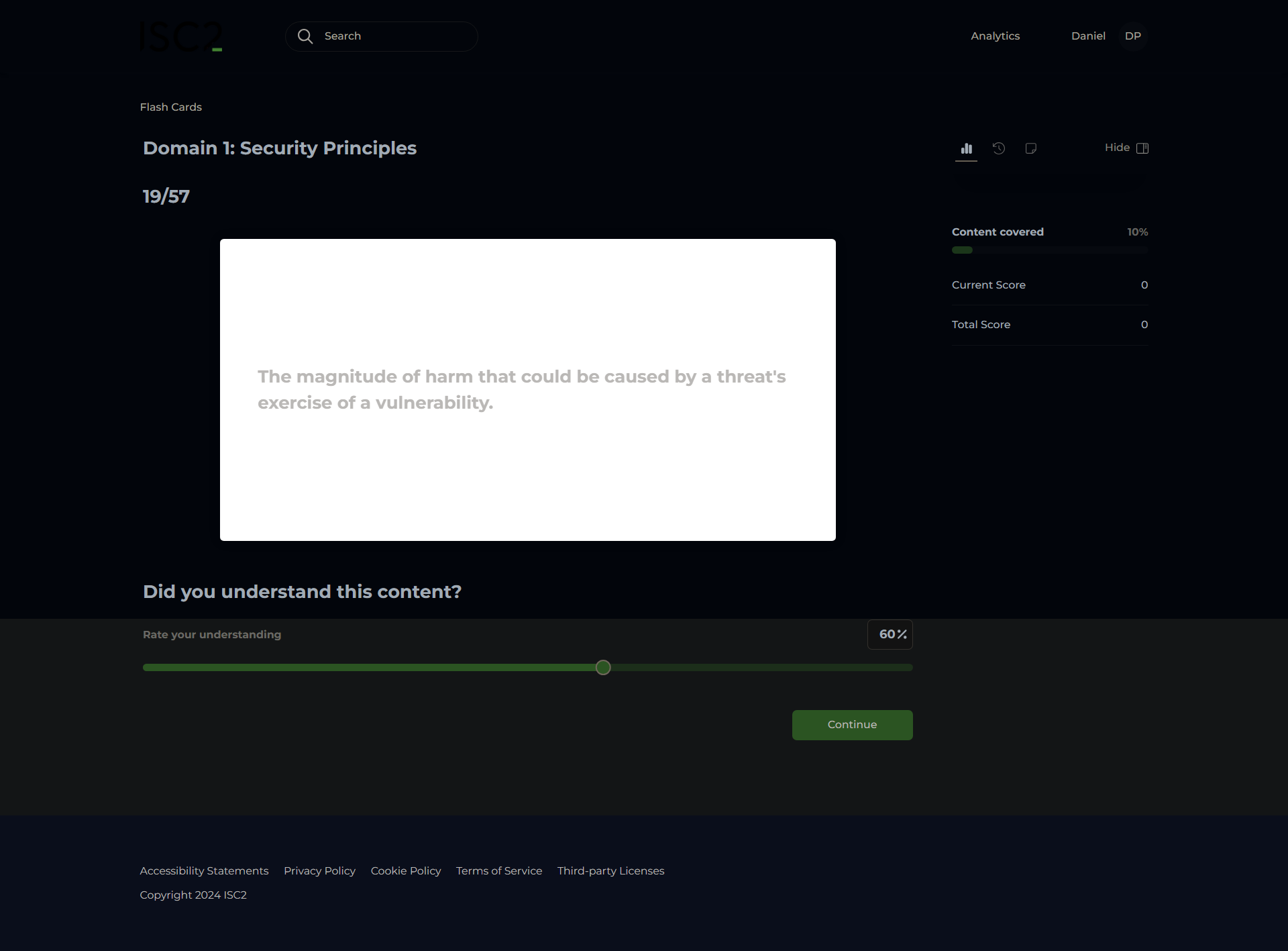
Impact
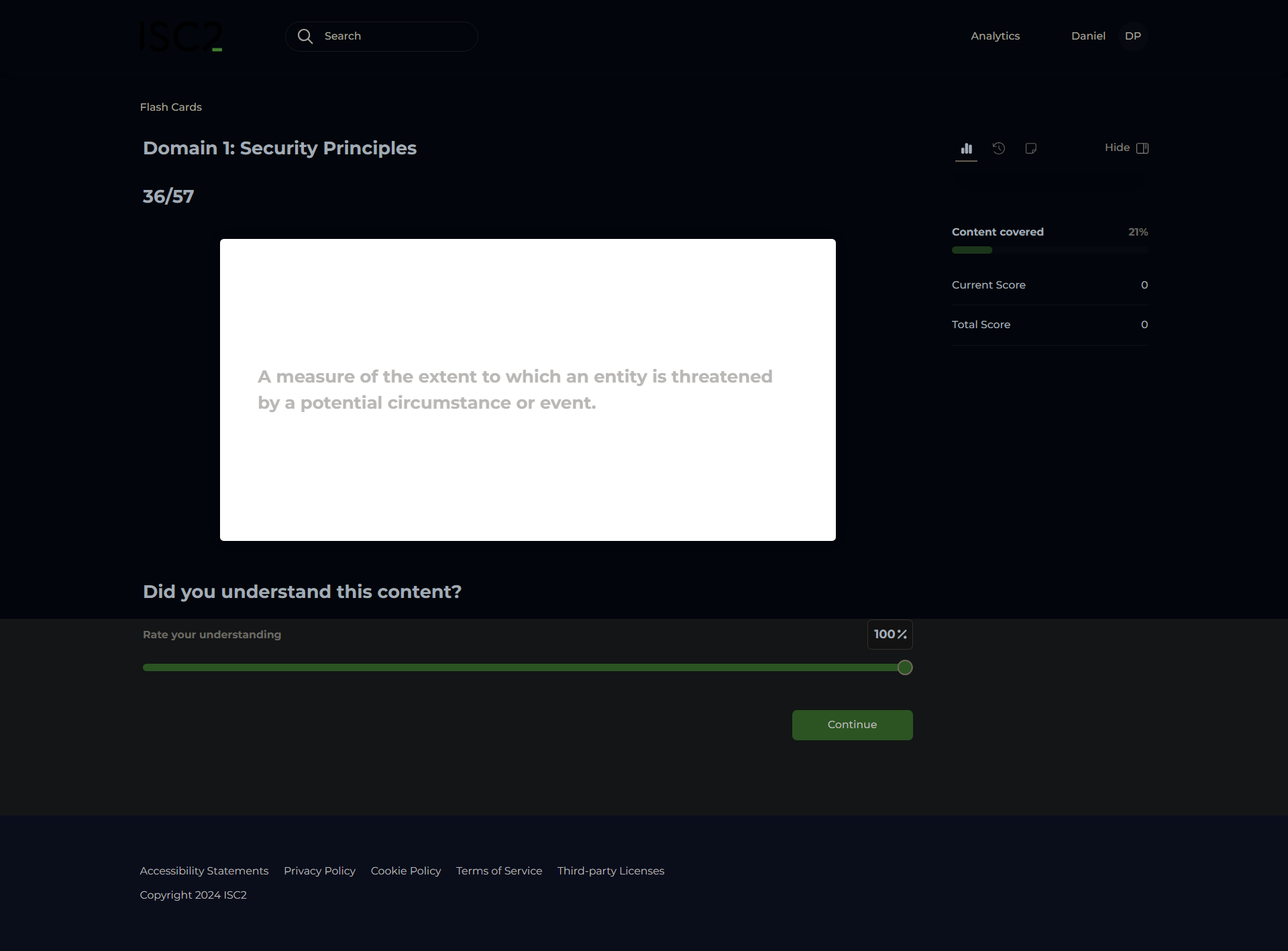
Information Security Risk
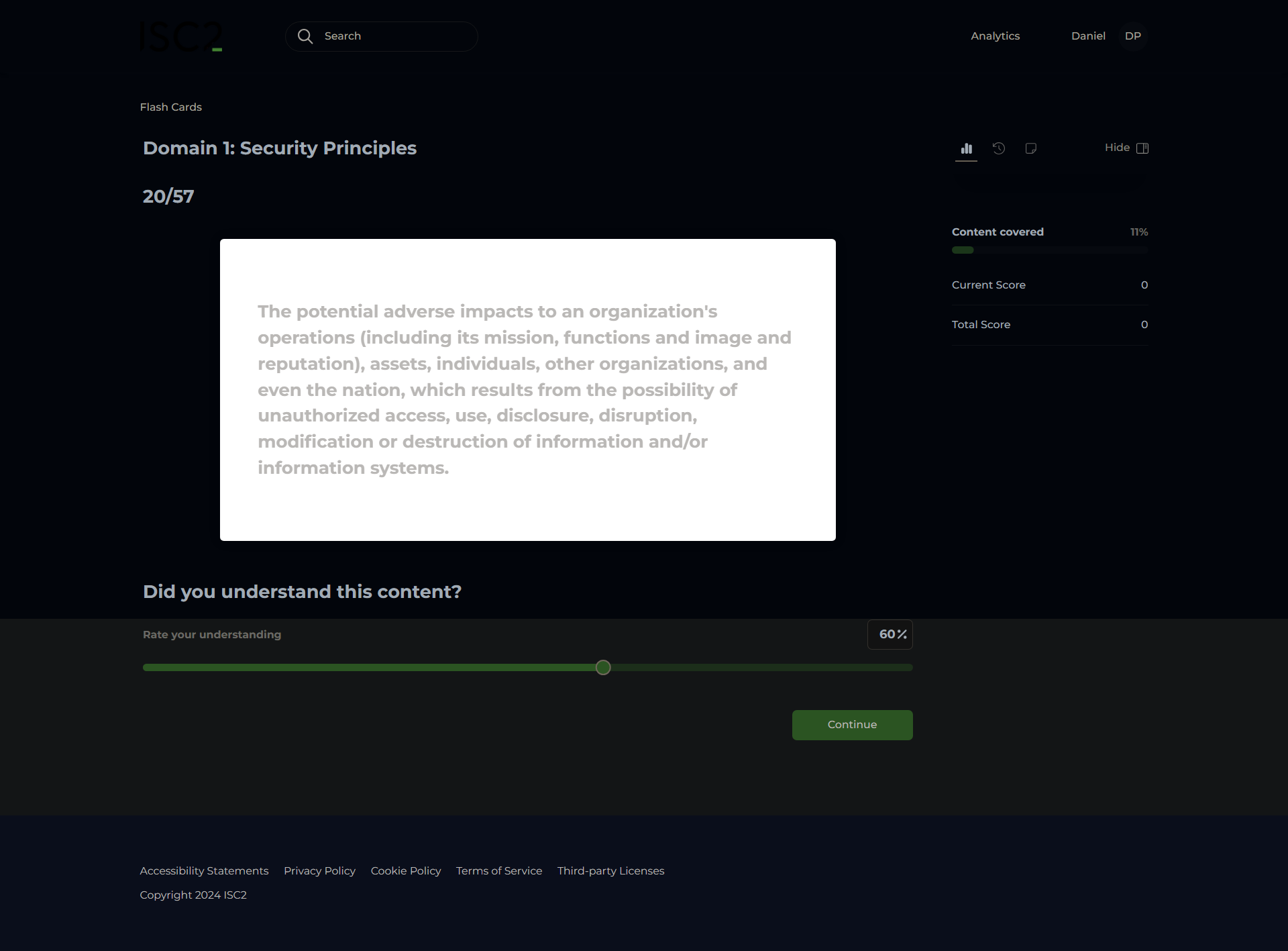
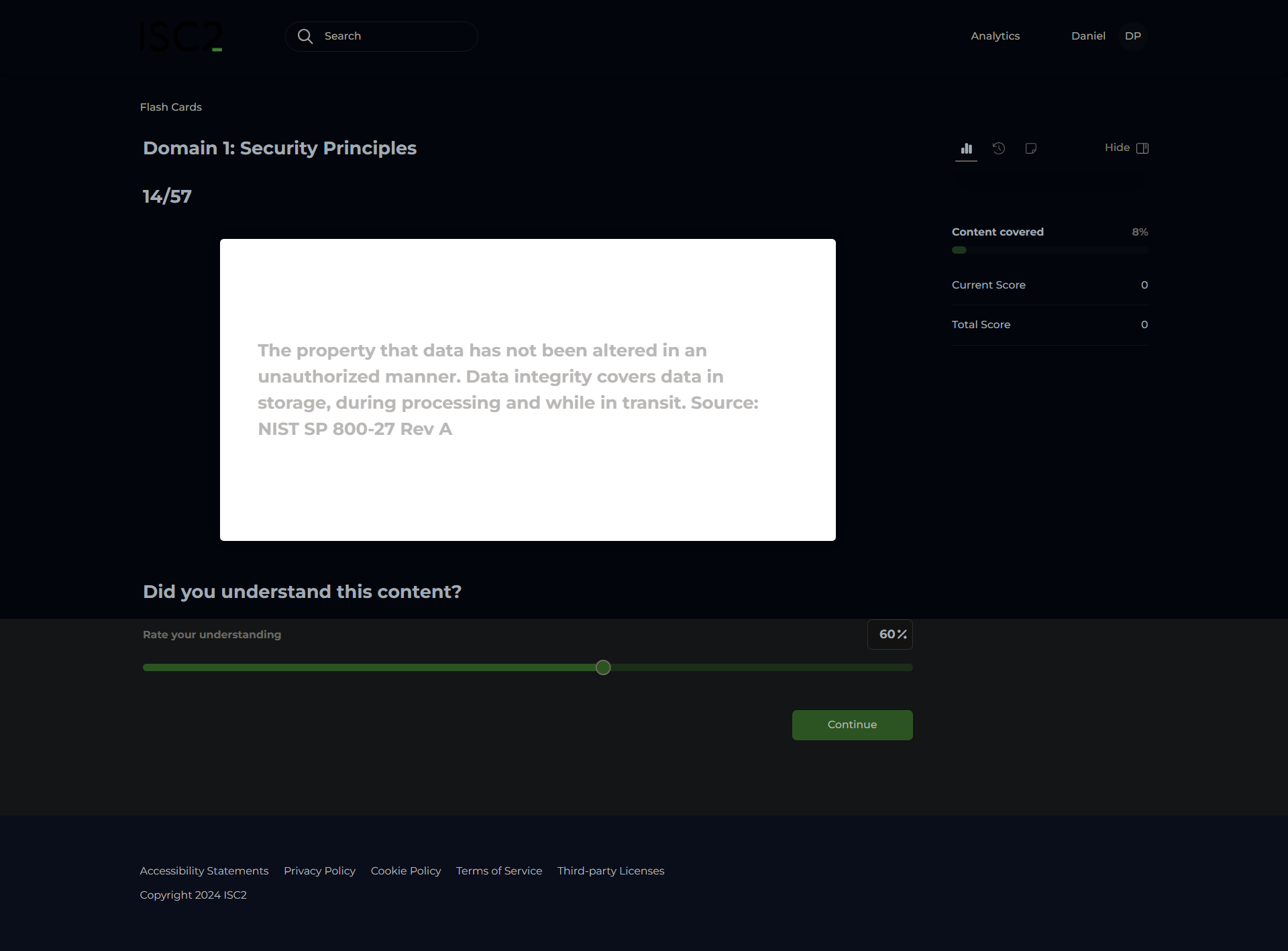
Integrity
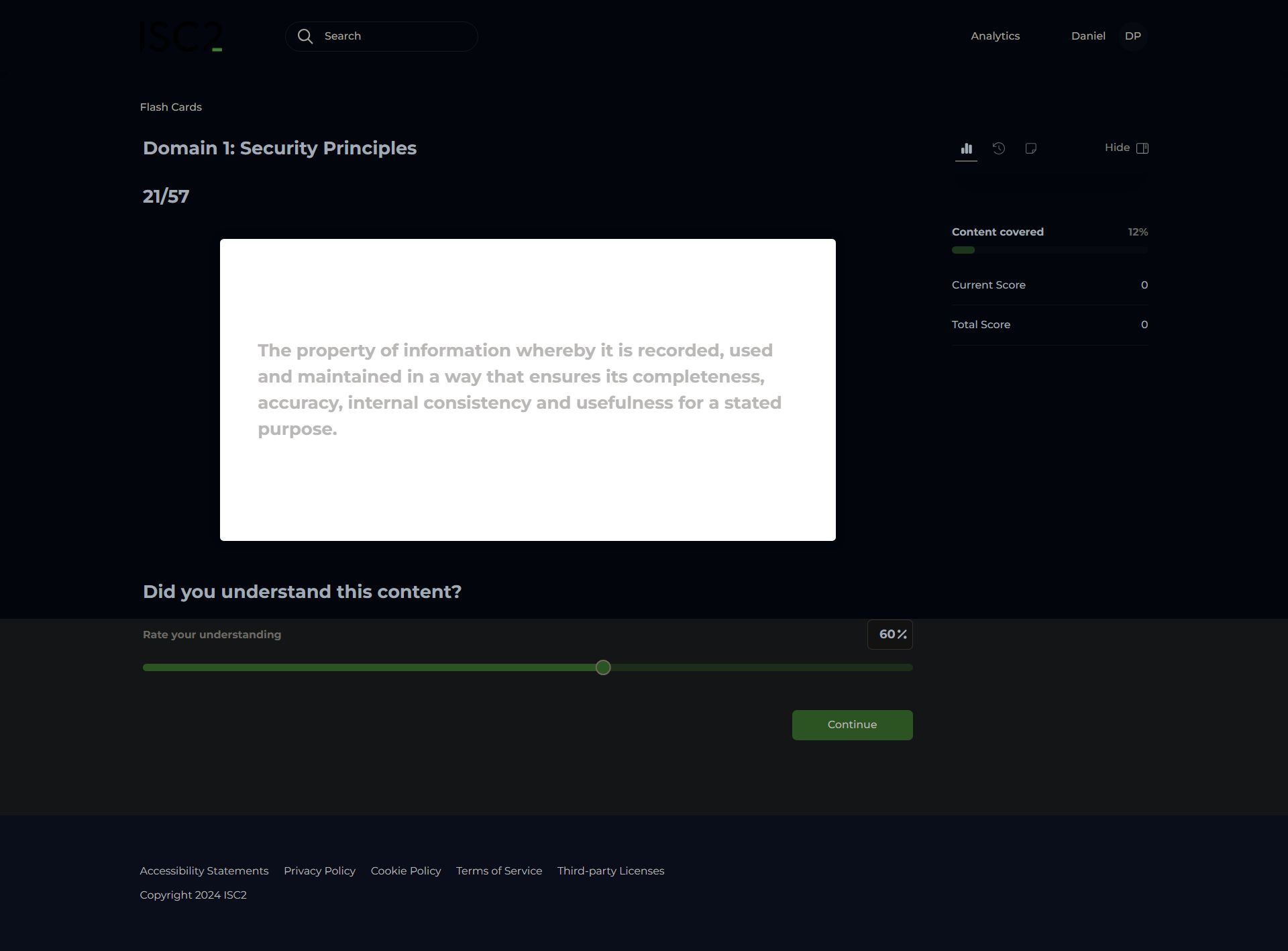
International Organization Standards (ISO)
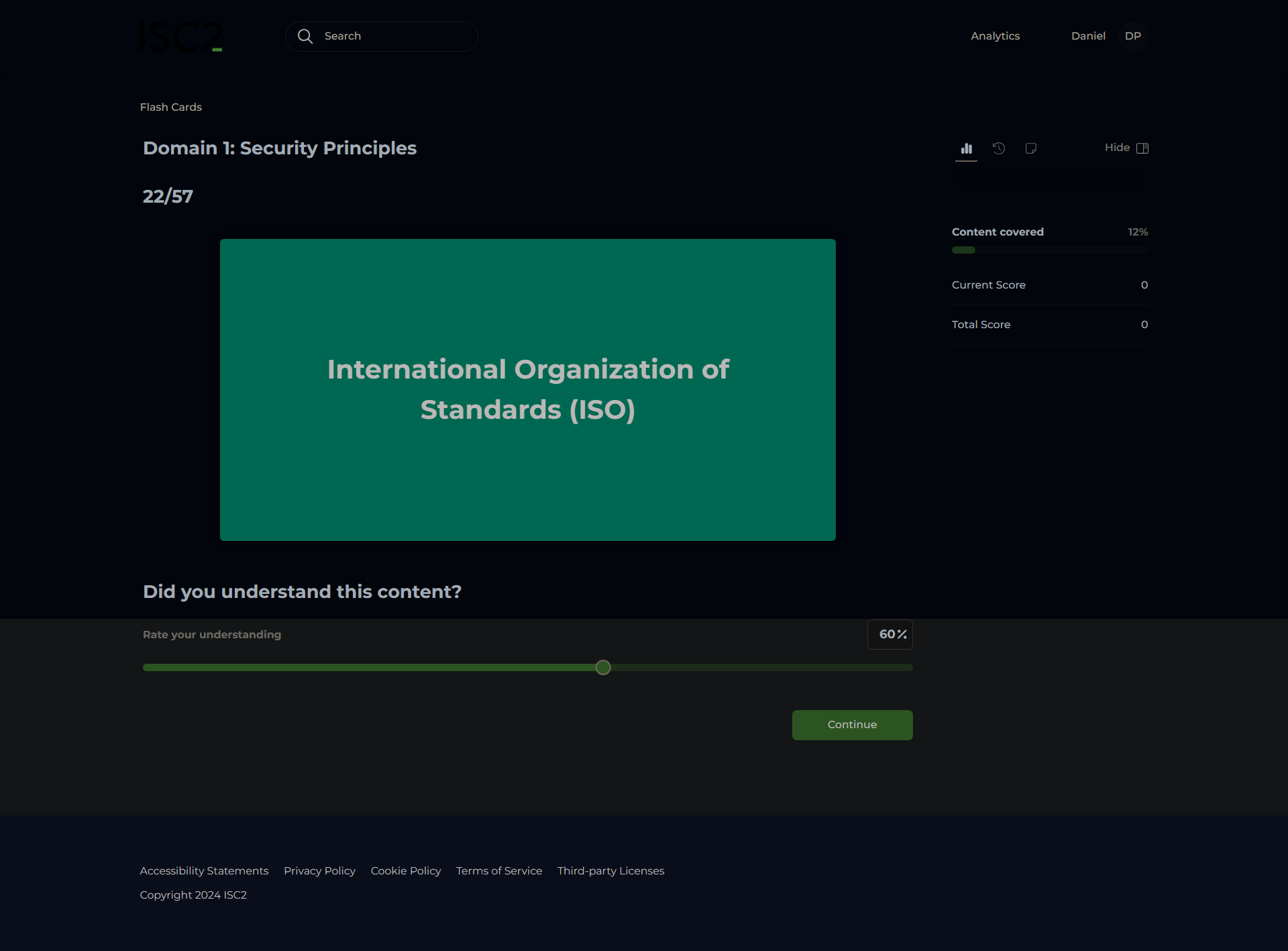
Internet Engineering Task Force (IETF)
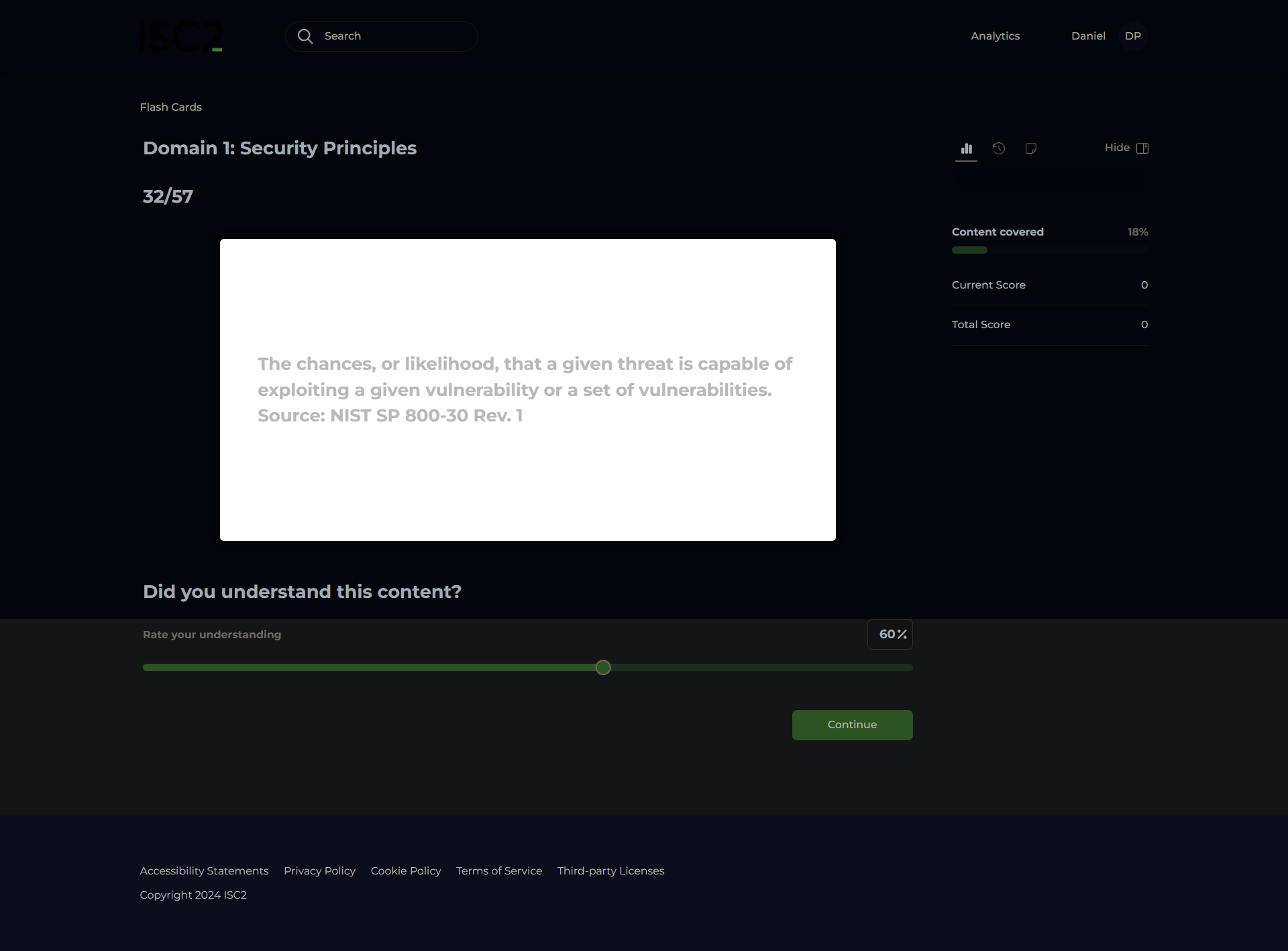
Likelihood
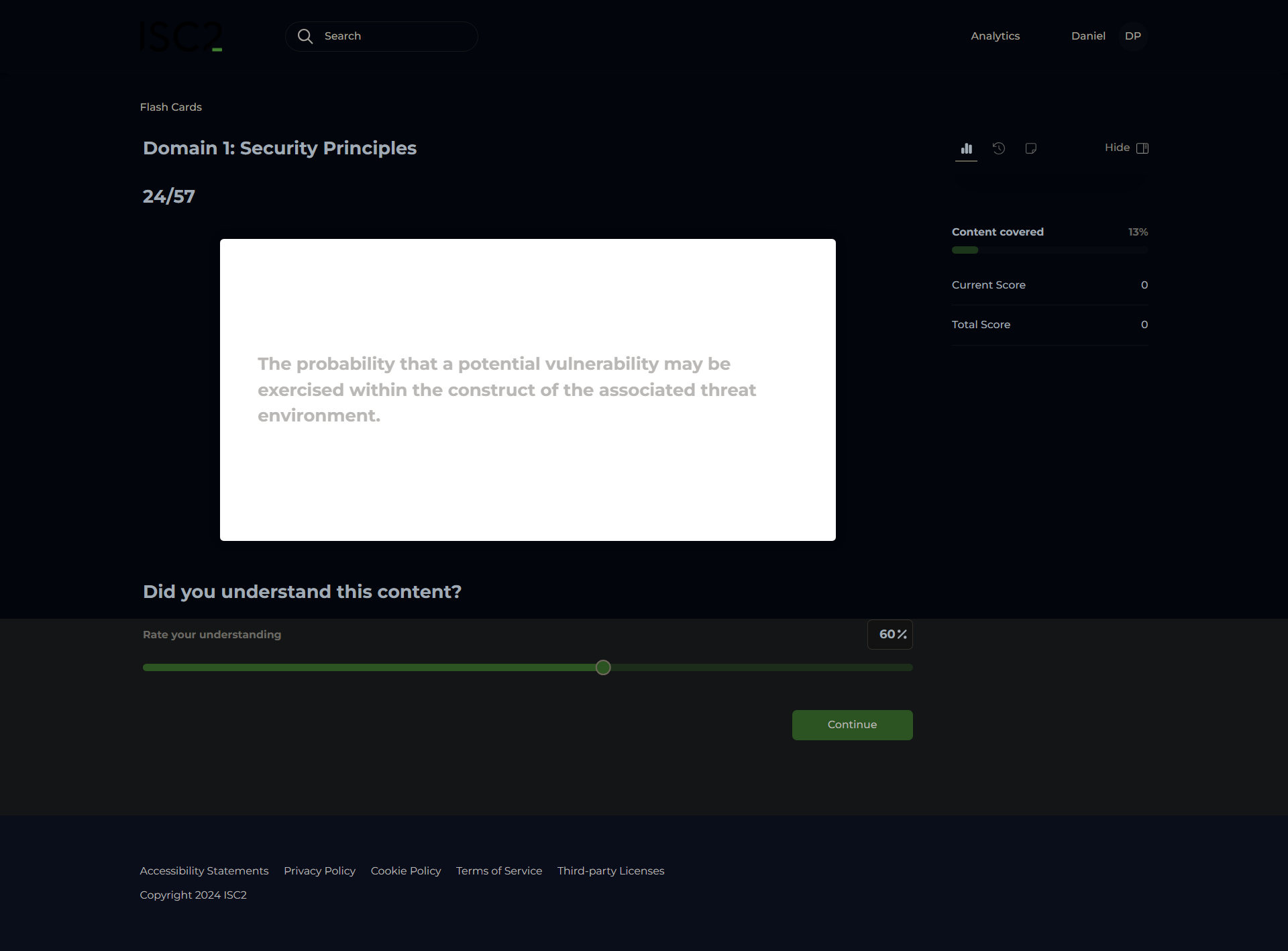
Likelihood of Occurrence
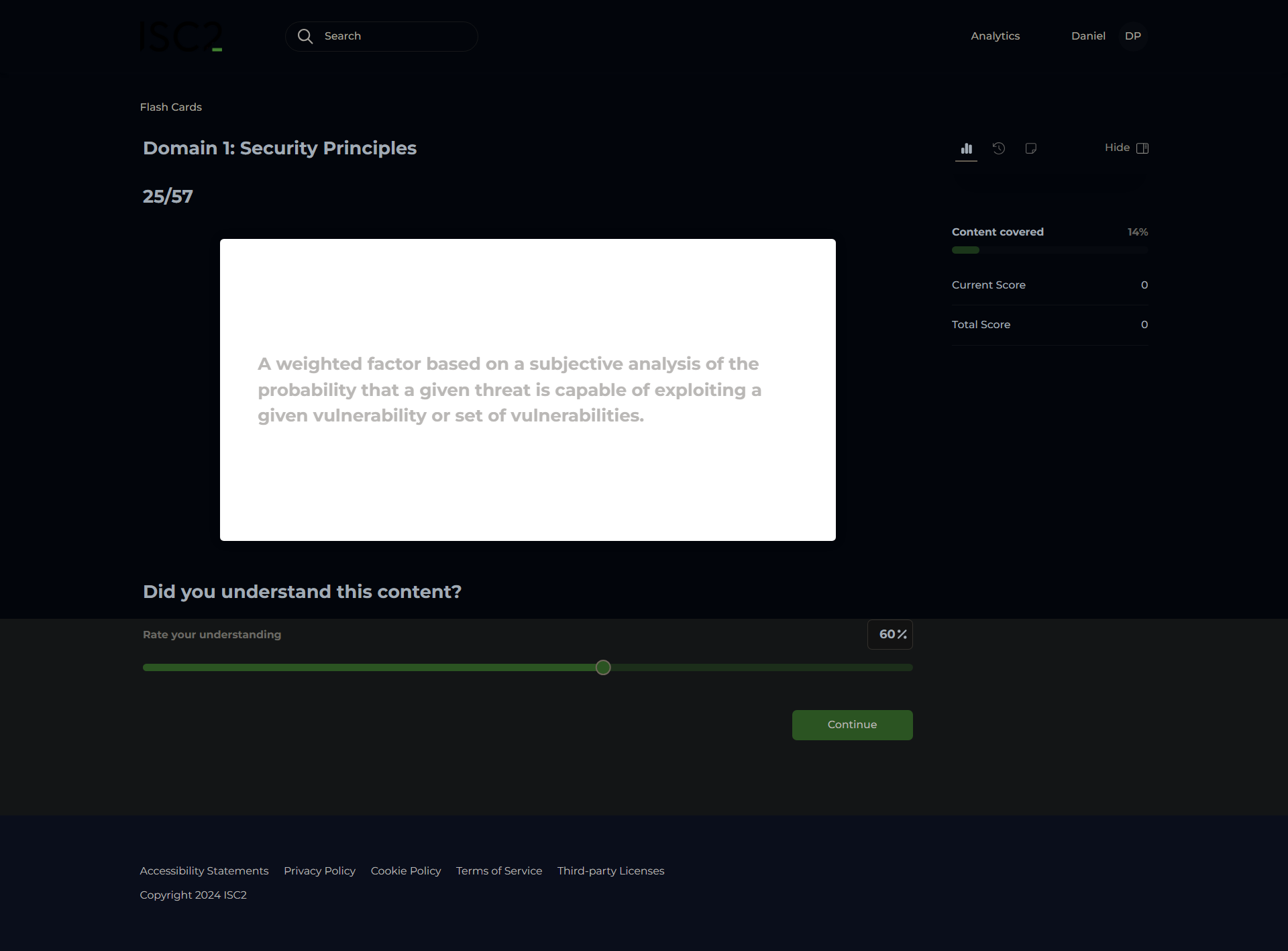
Multi-Factor Authentication
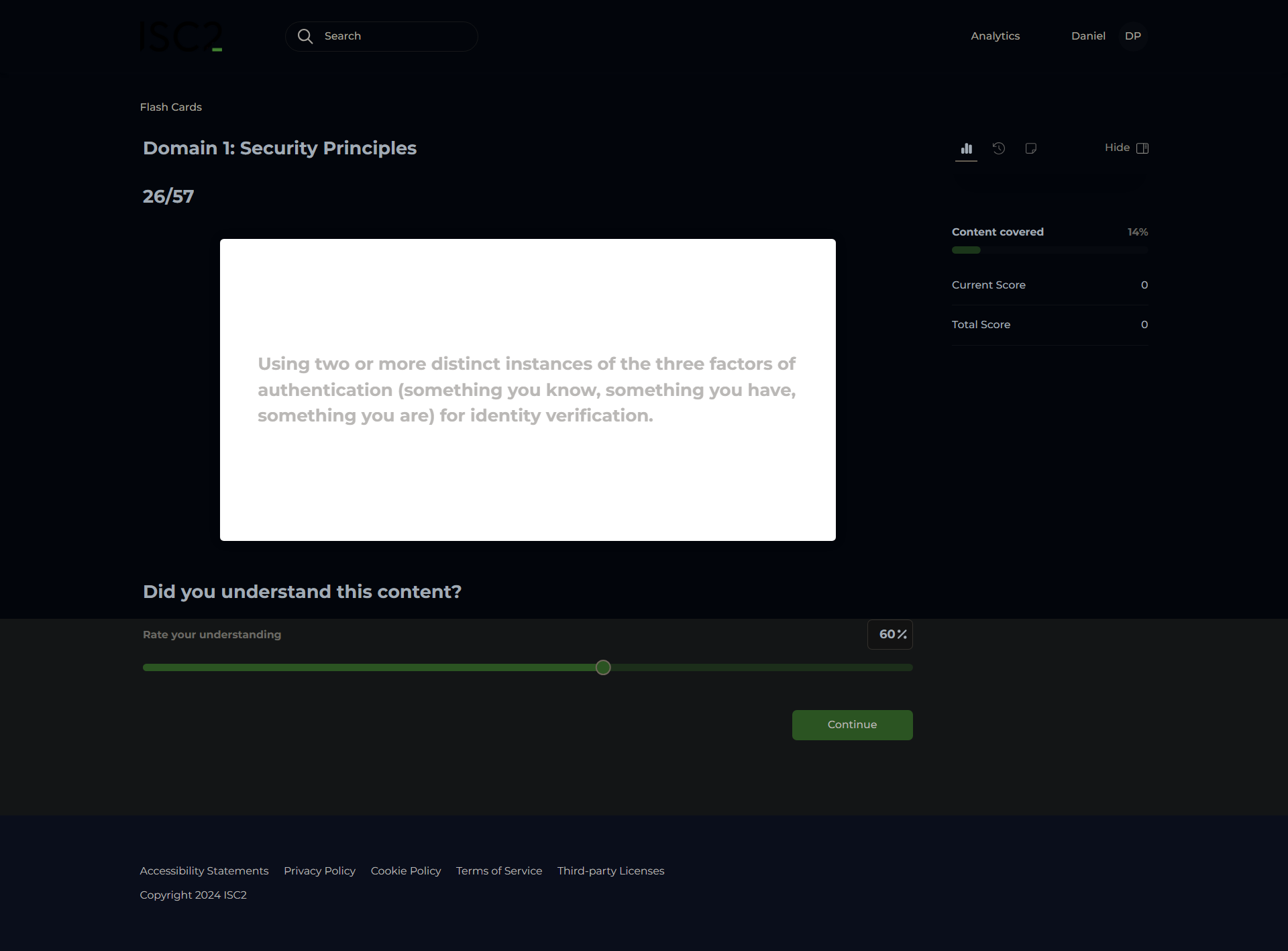
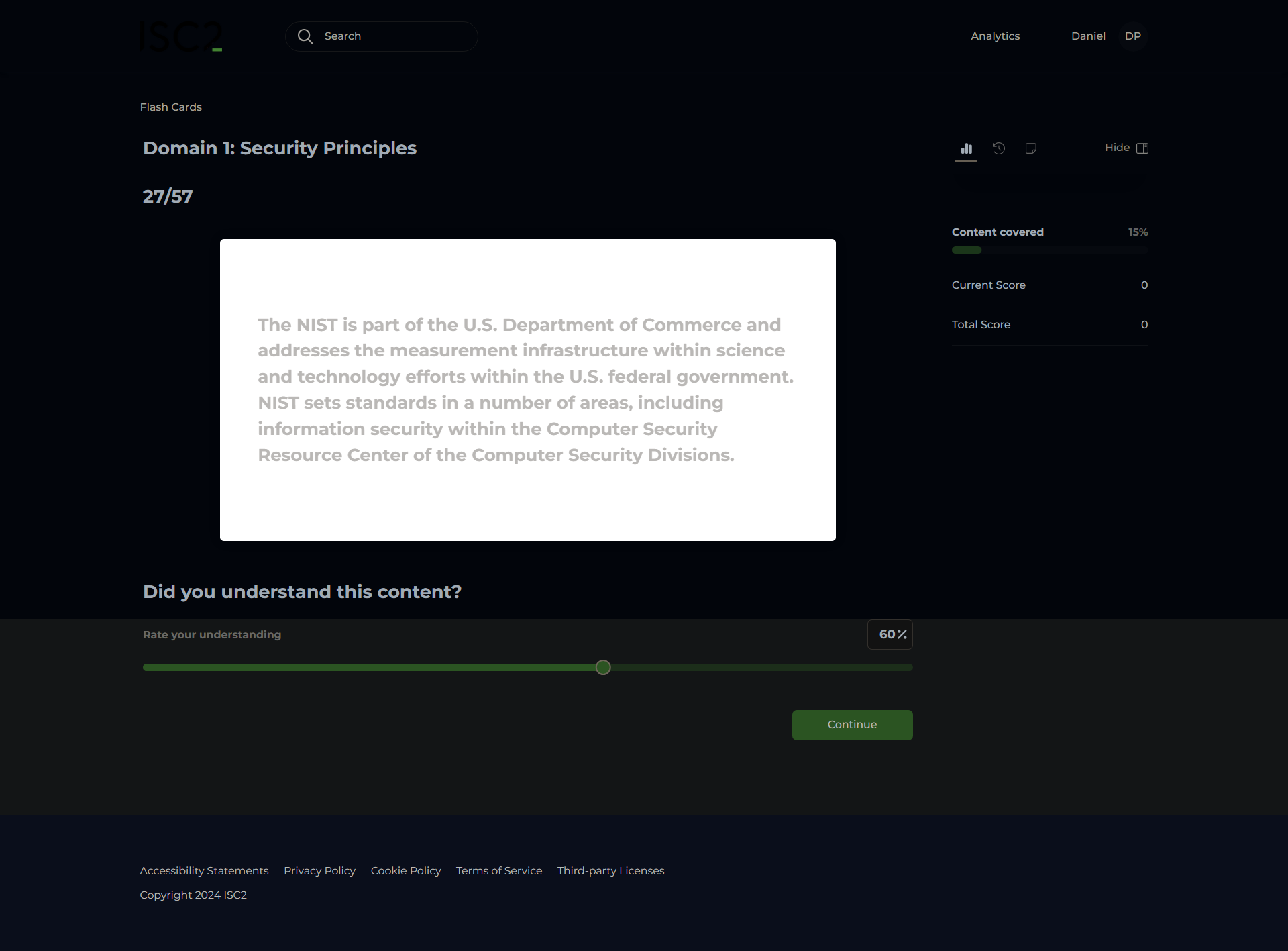
National Institutes of Standards and Technology (NIST)
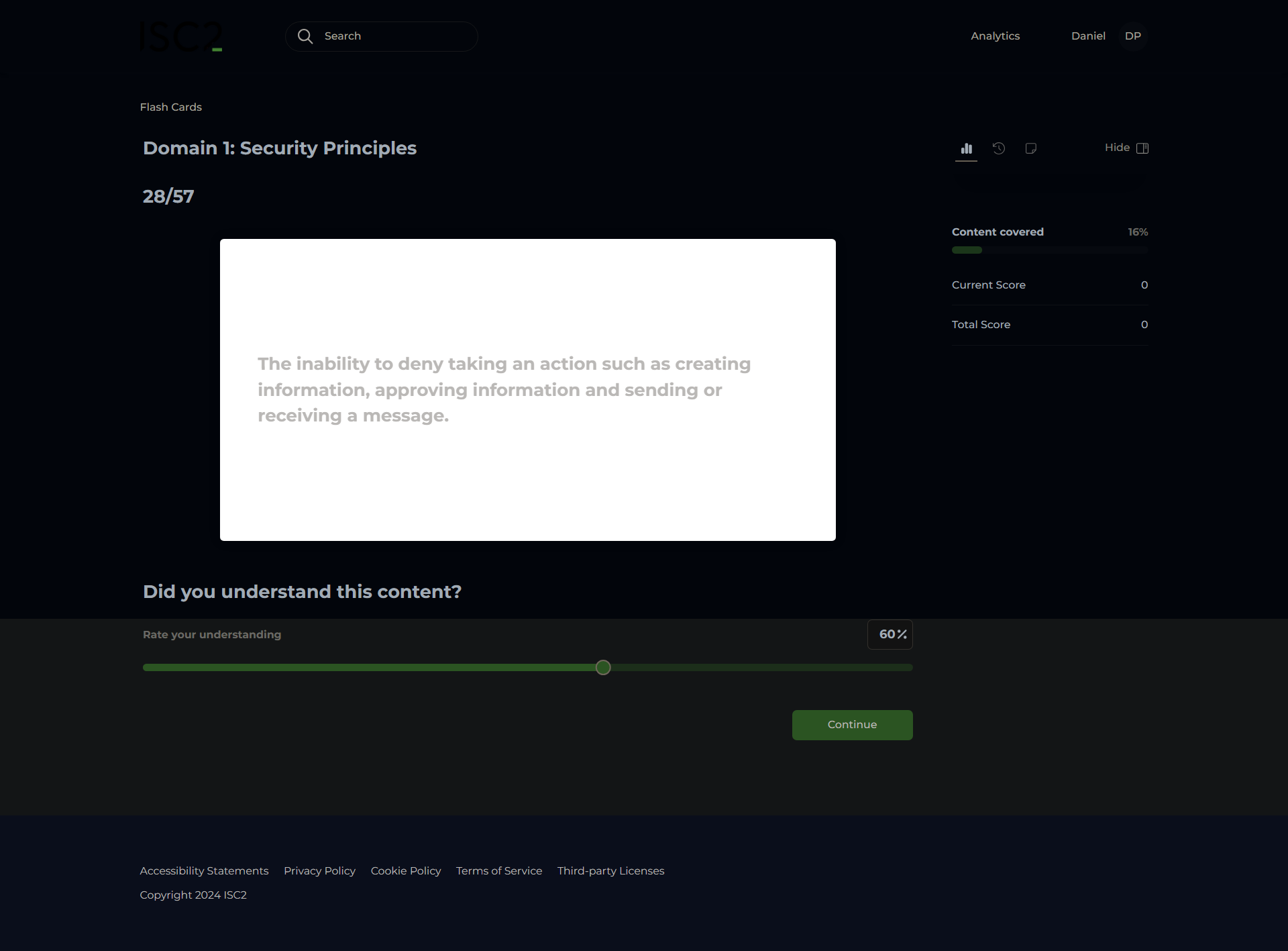
Non-repudiation
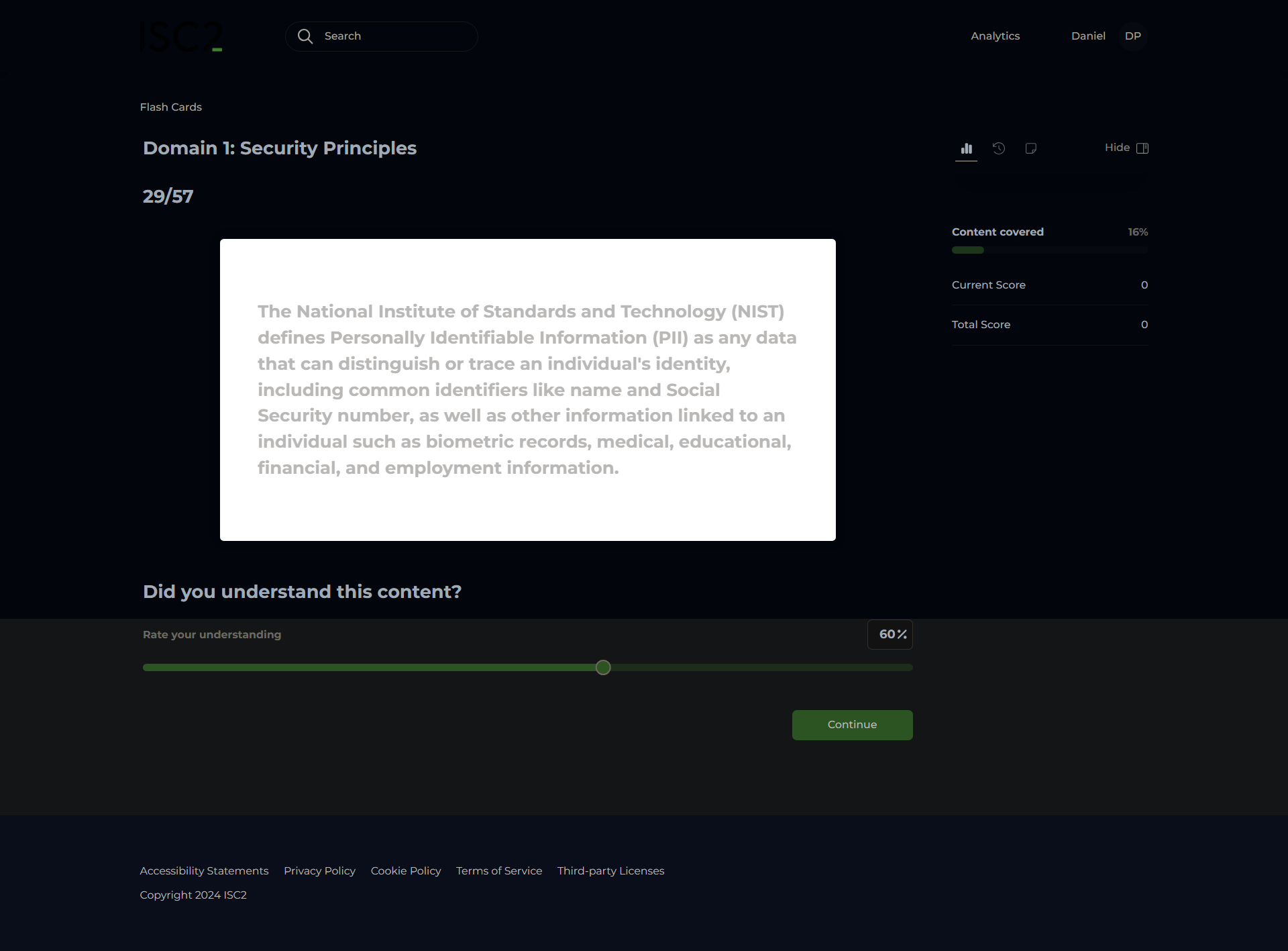
Personally Identifiable Information (PII)
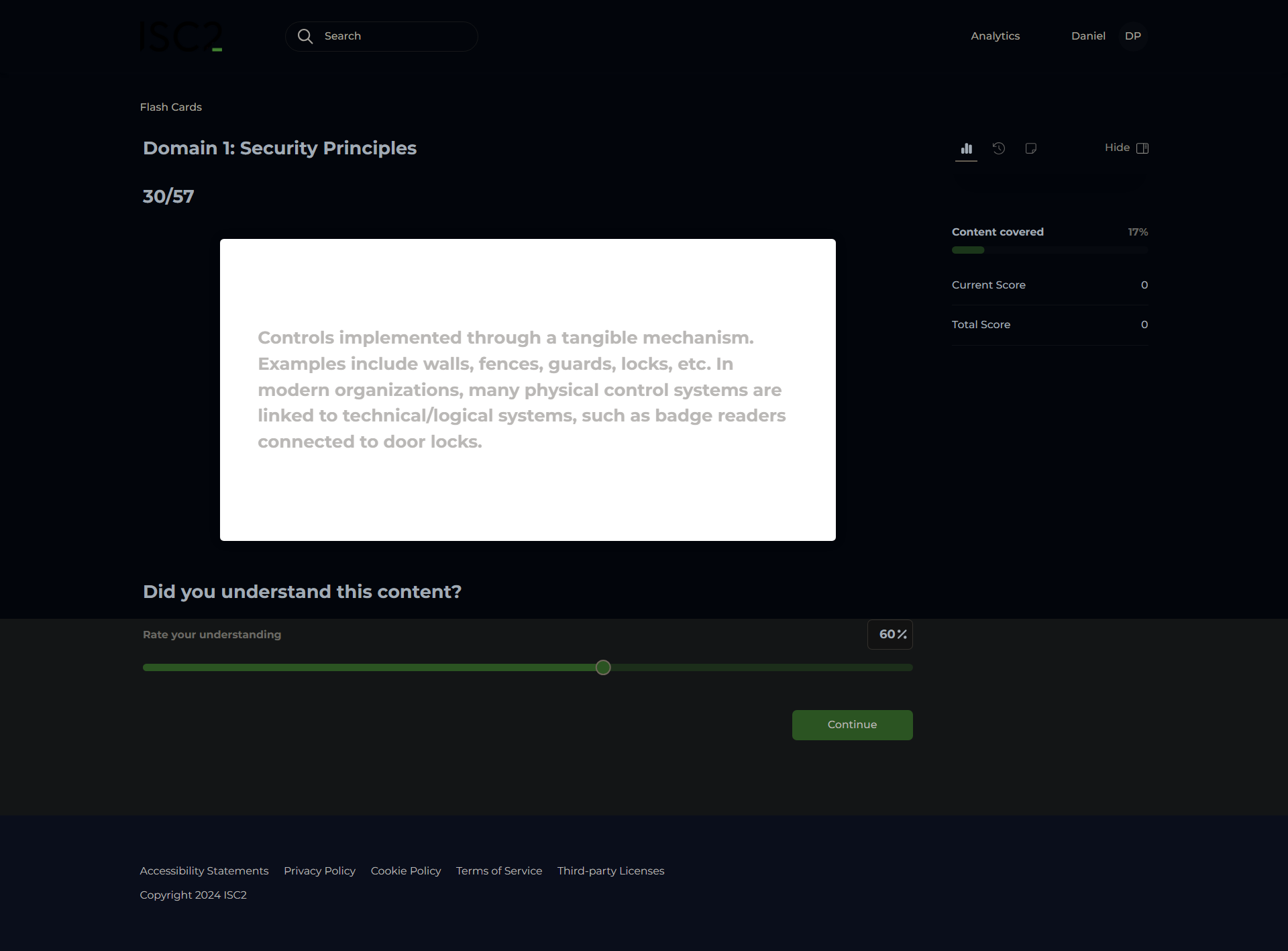
Physical Controls
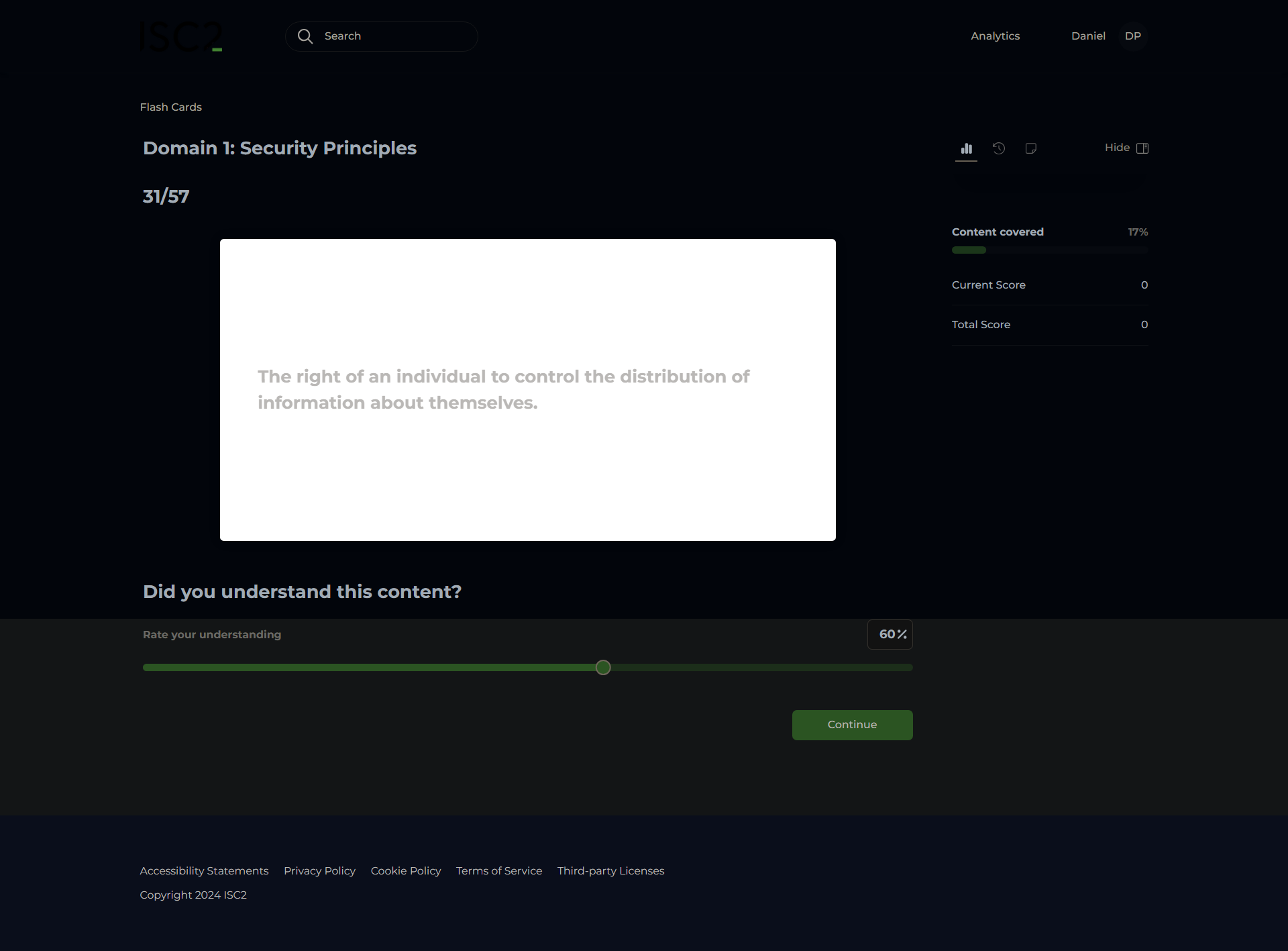
Privacy
Probability
Protected Health Information
Qualitative Risk Analysis
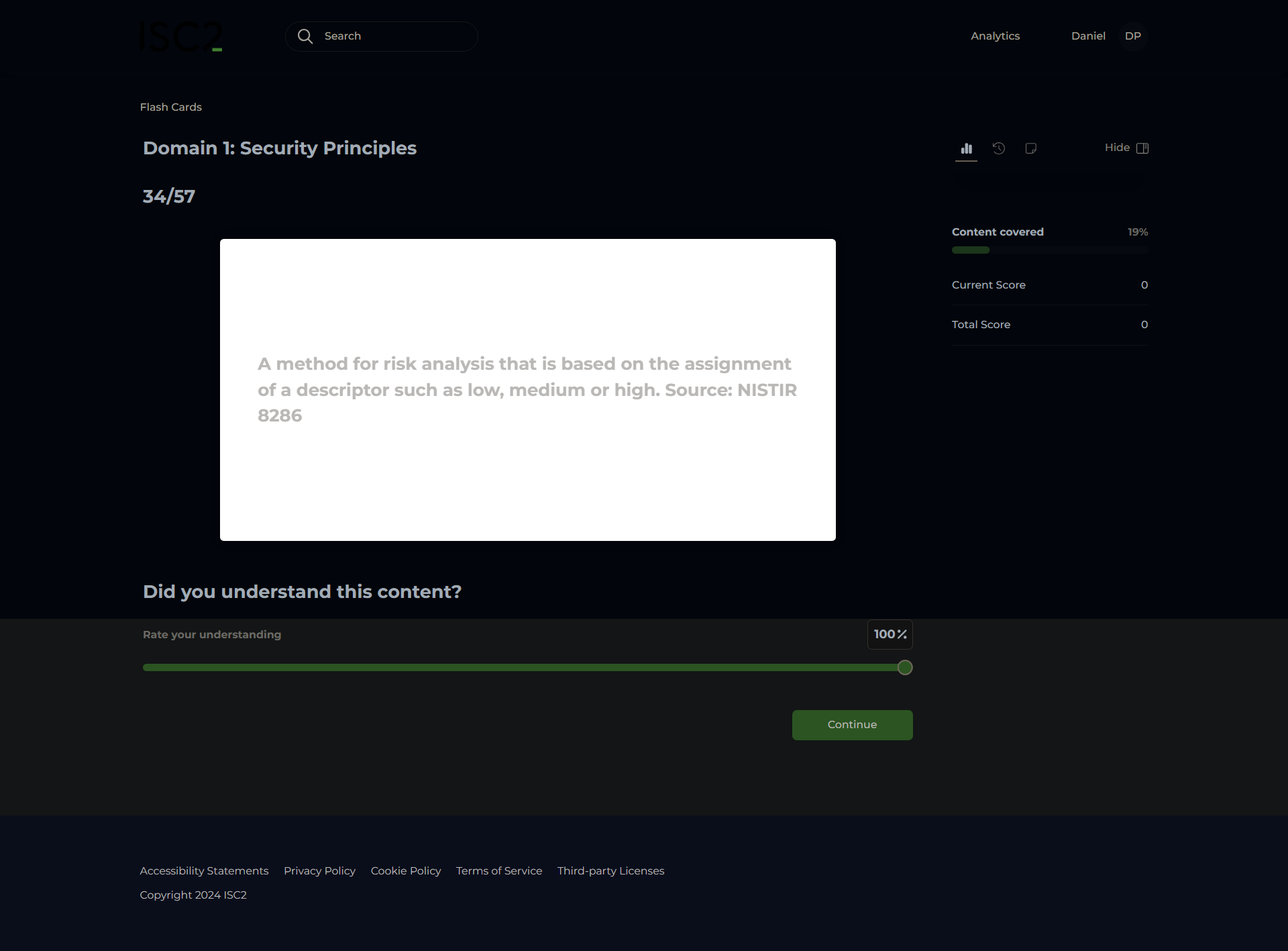
Risk
Risk Acceptance
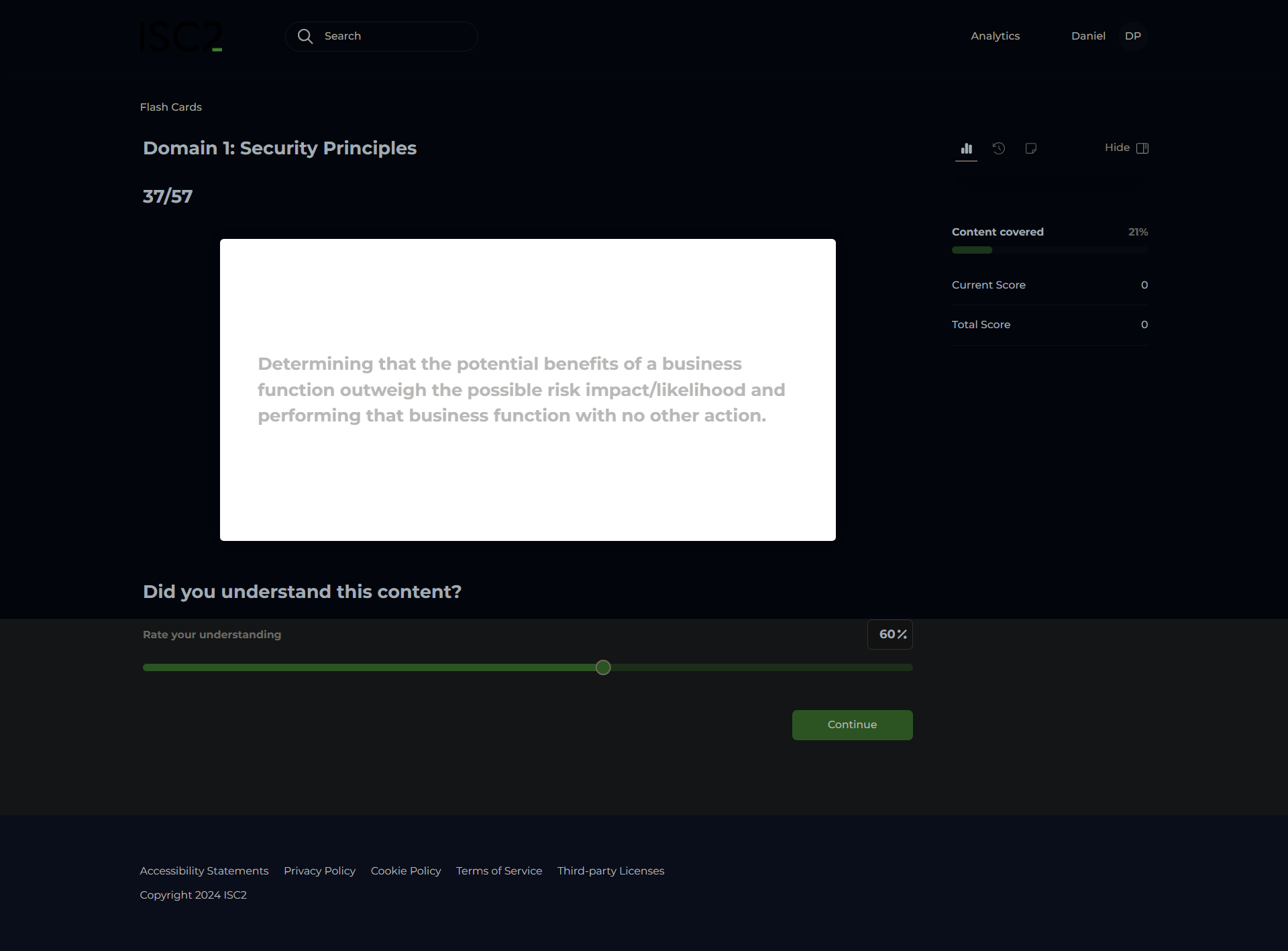
Risk Assessment
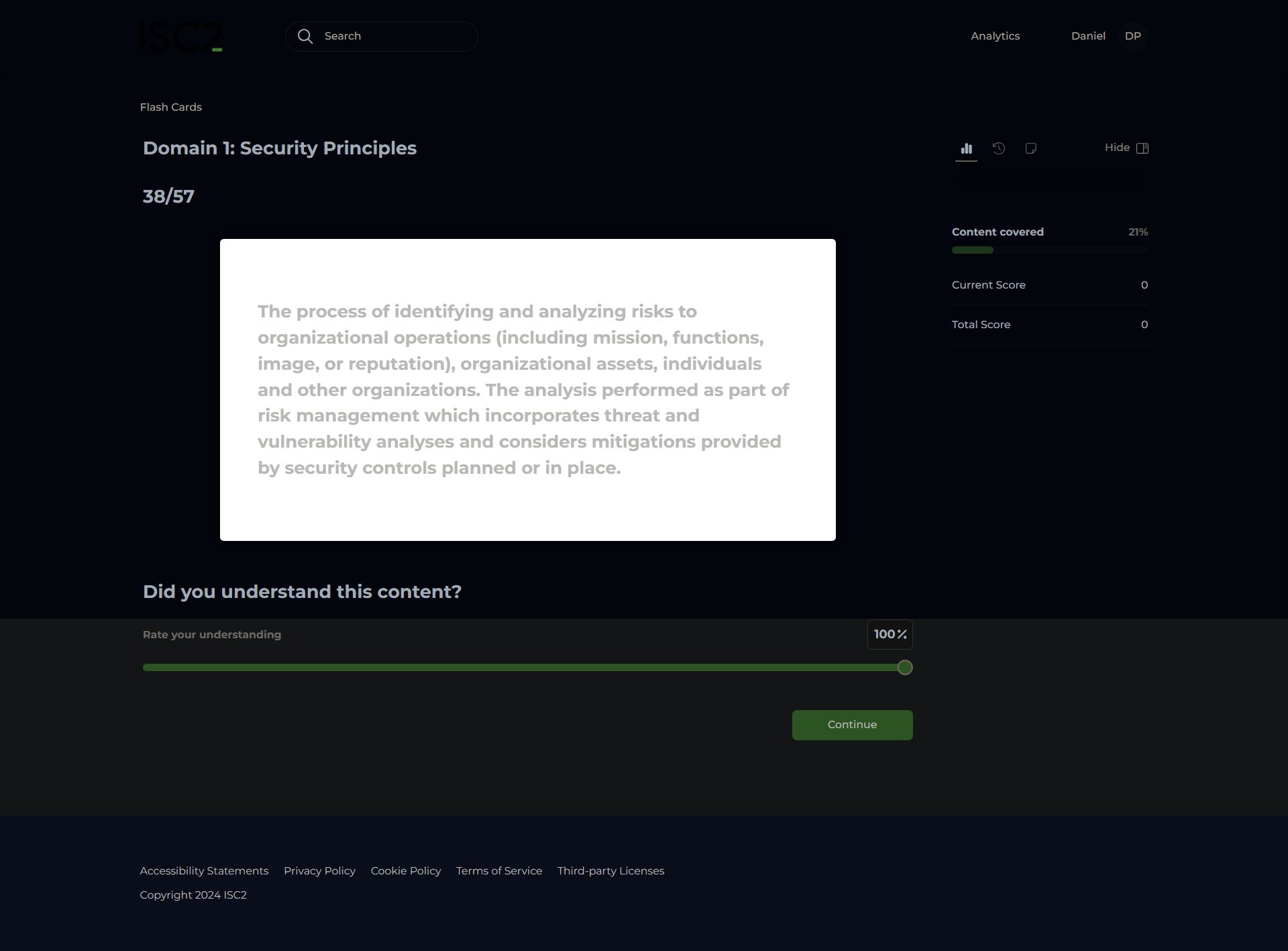
Risk Avoidance
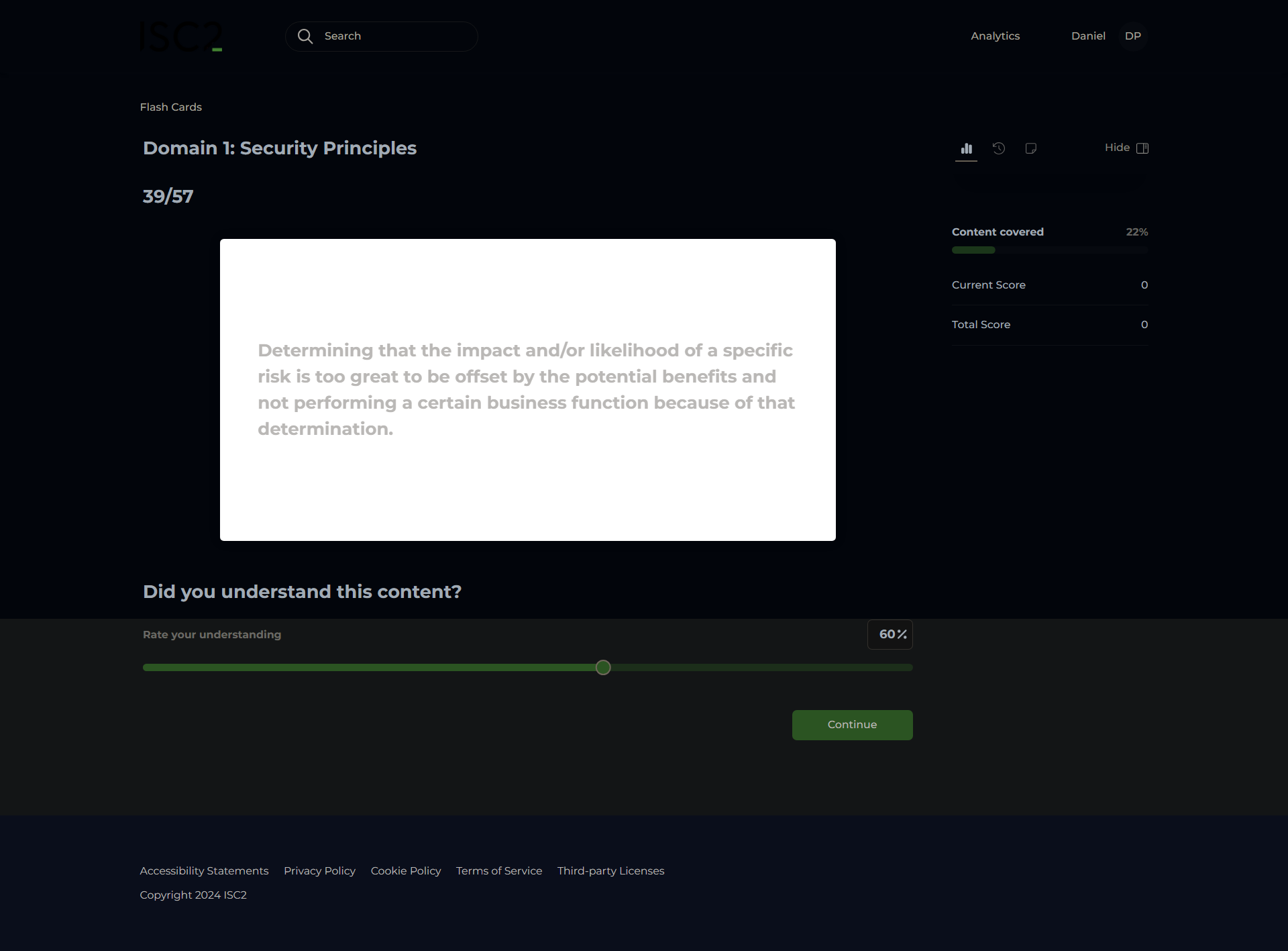
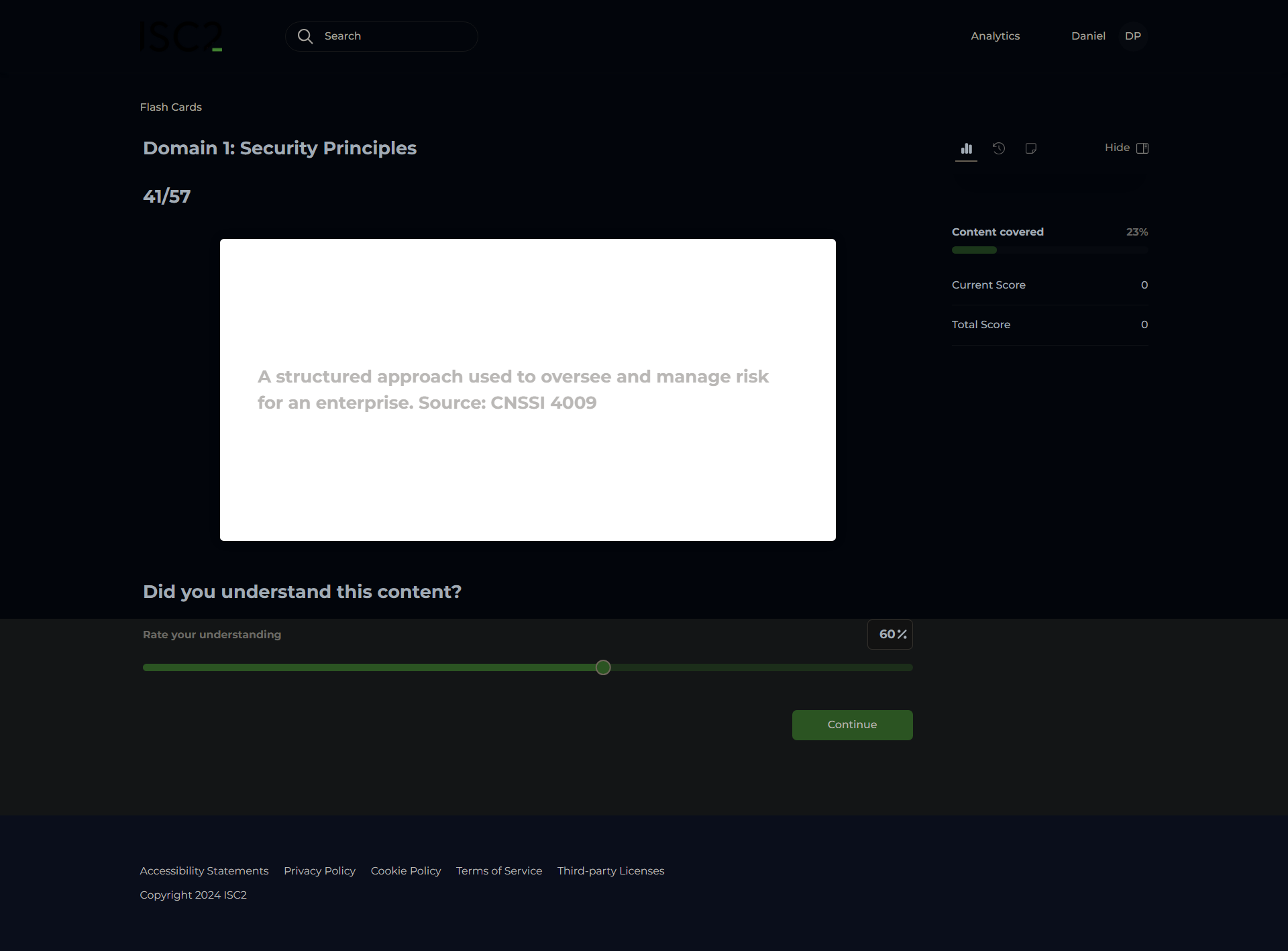
Risk Management
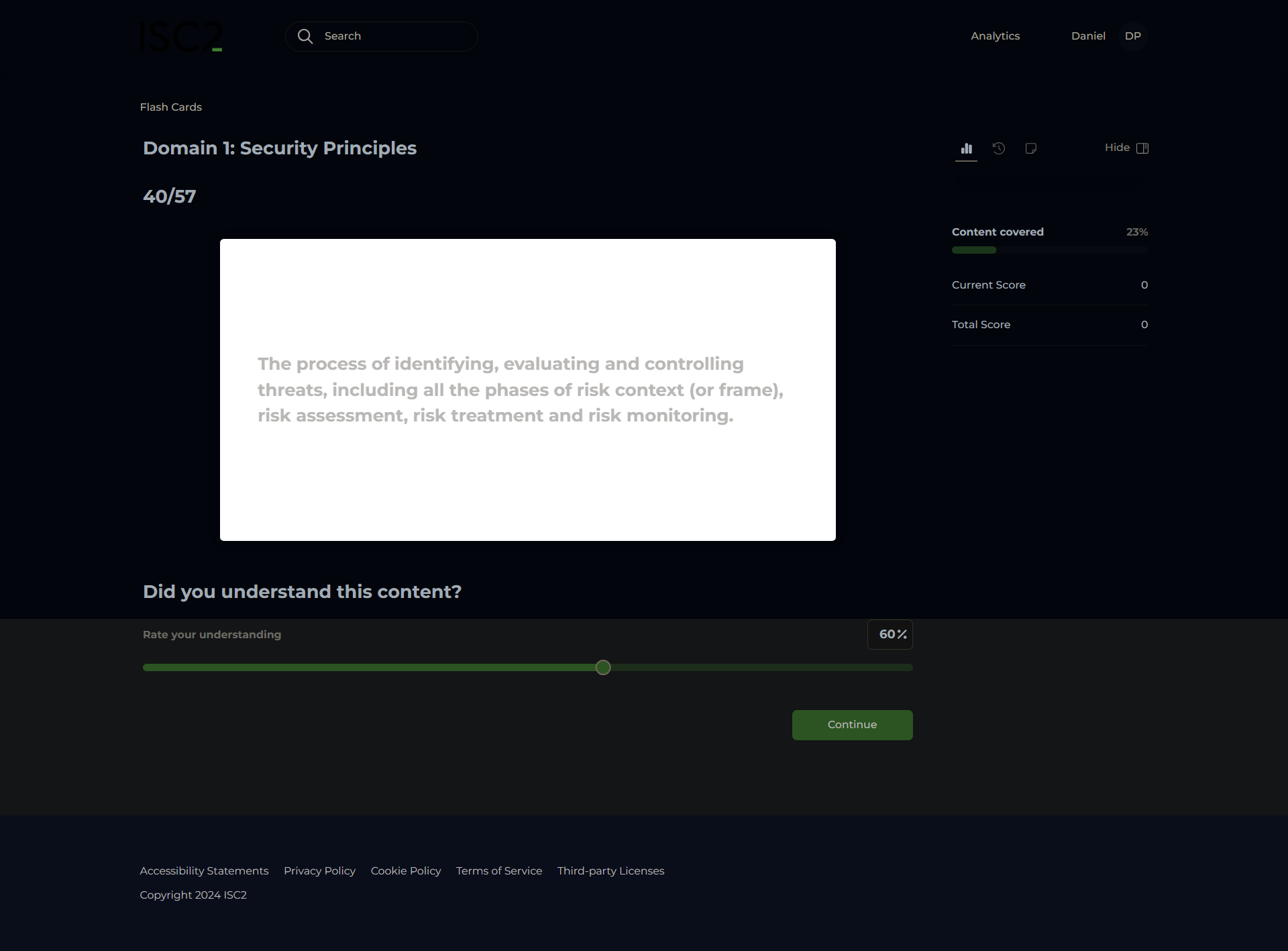
Risk Management Framework
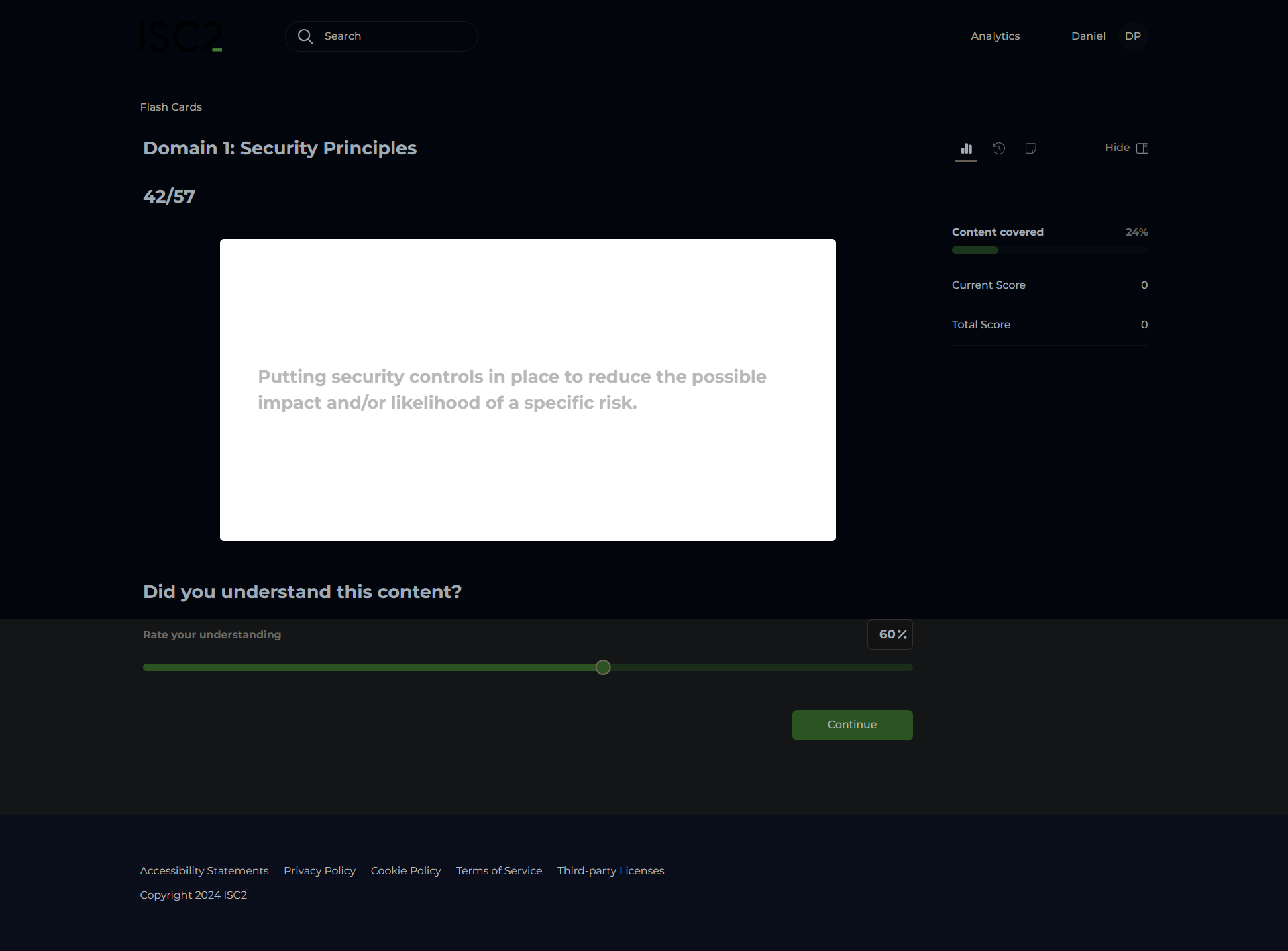
Risk Mitigation
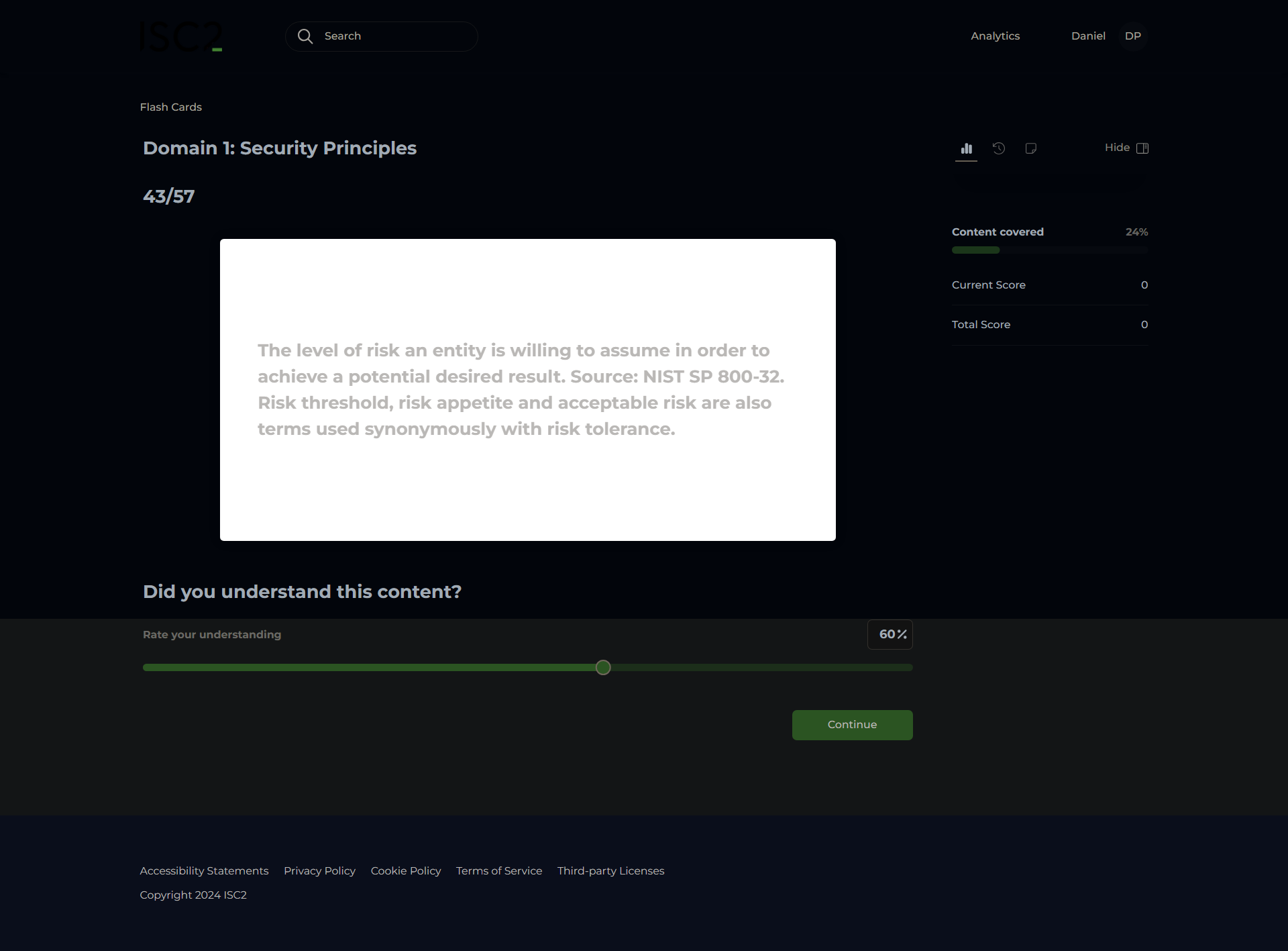
Risk Tolerance
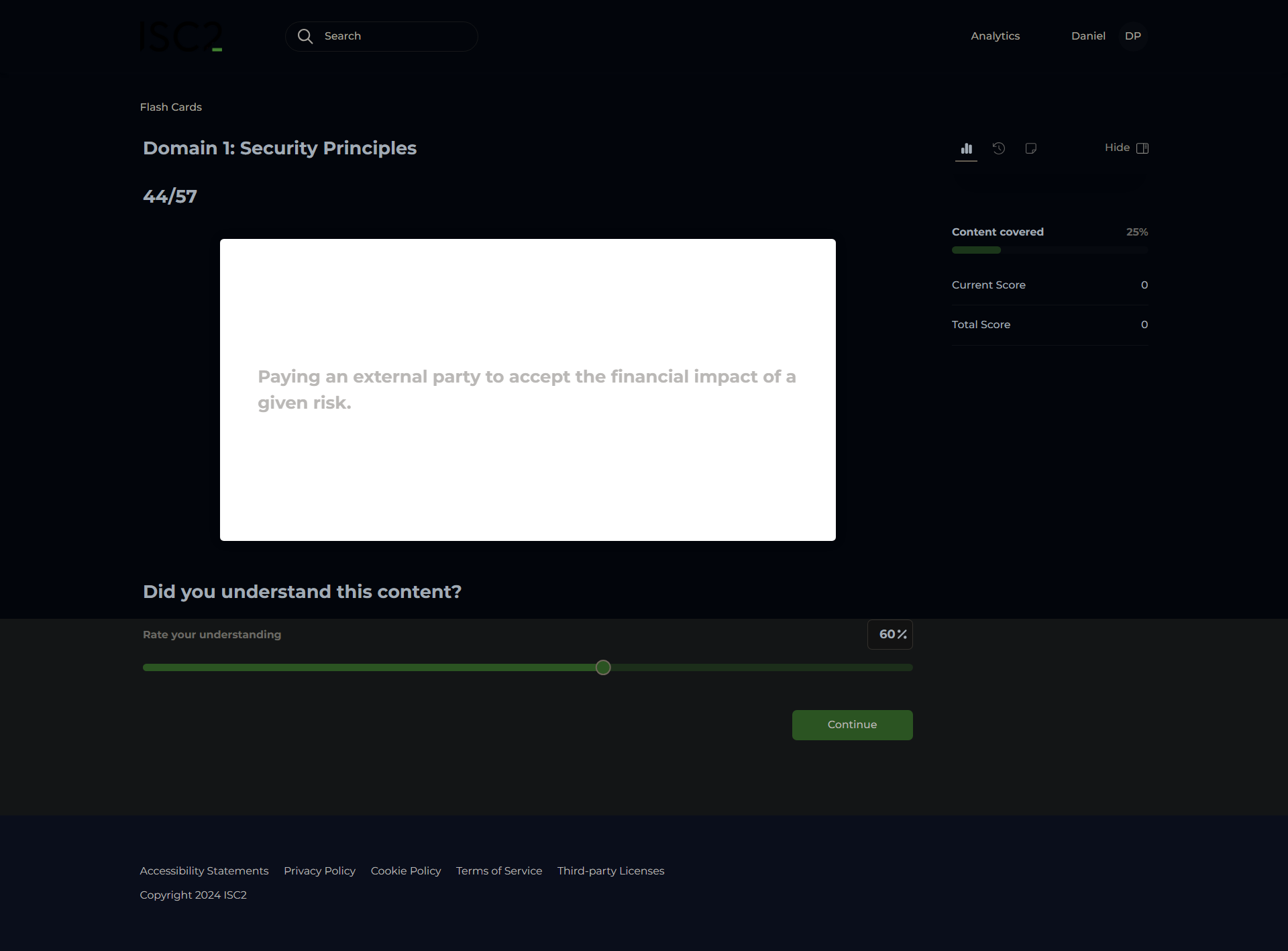
Risk Transference
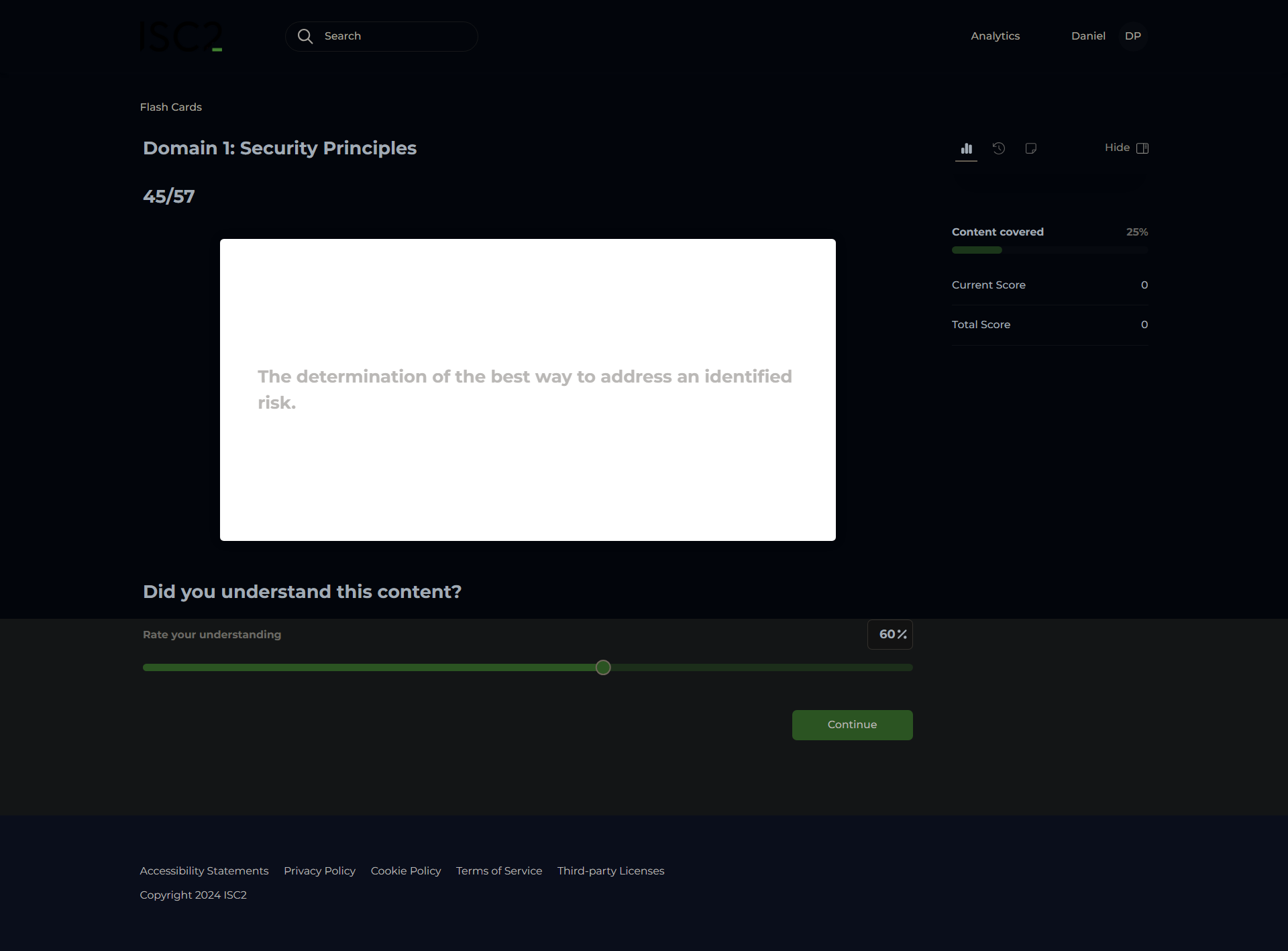
Risk Treatment
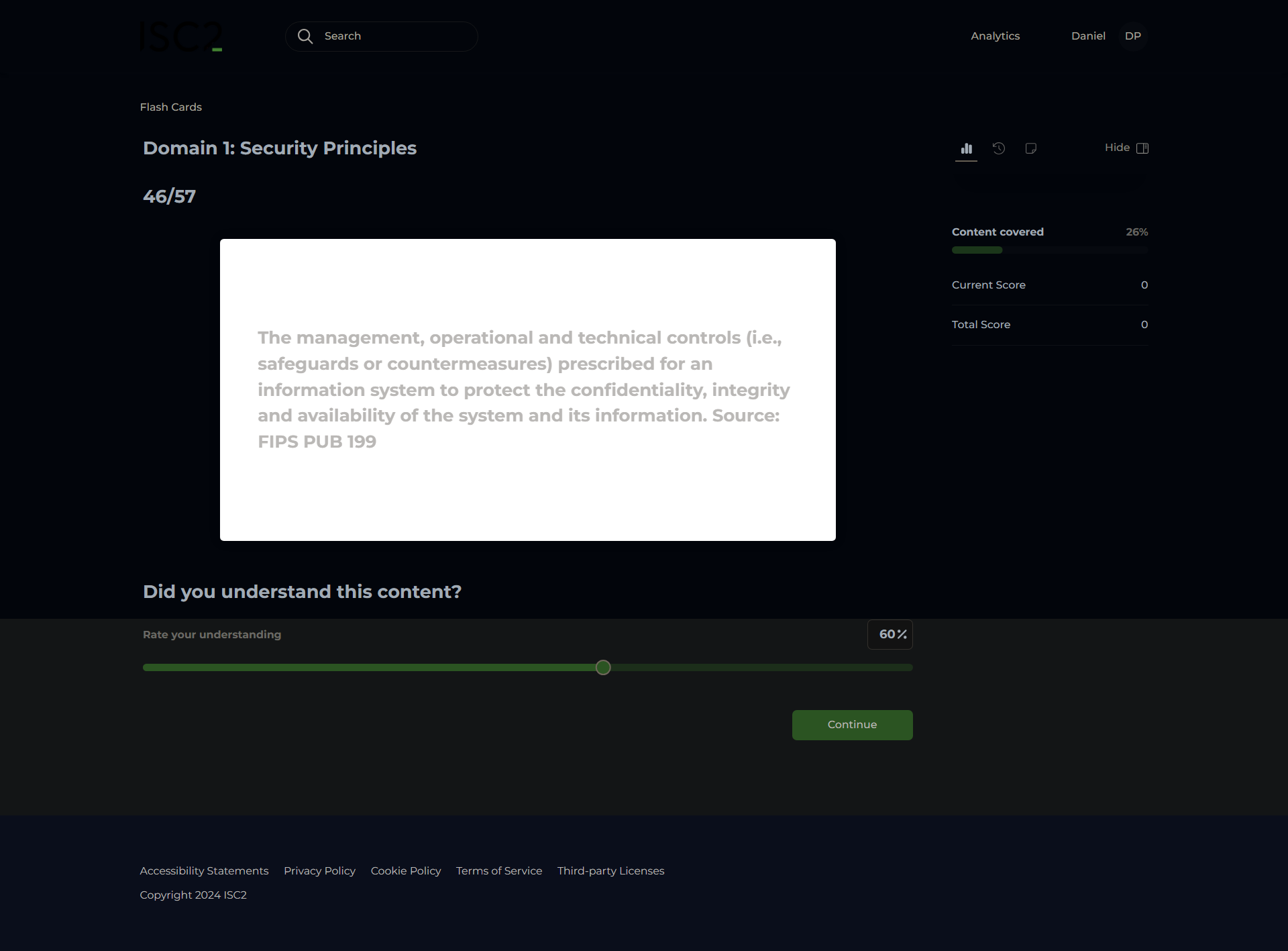
Security Controls
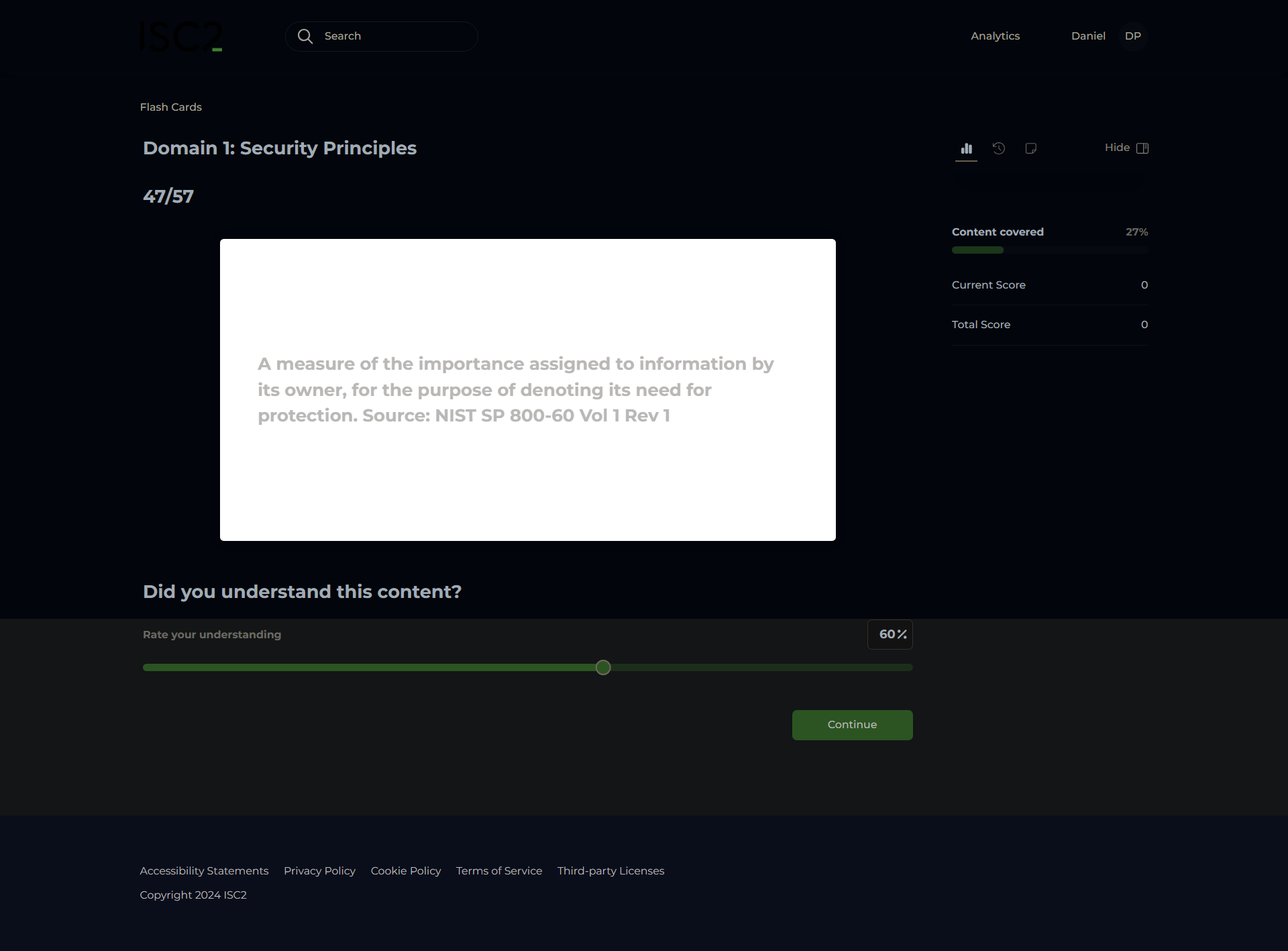
Sensitivity
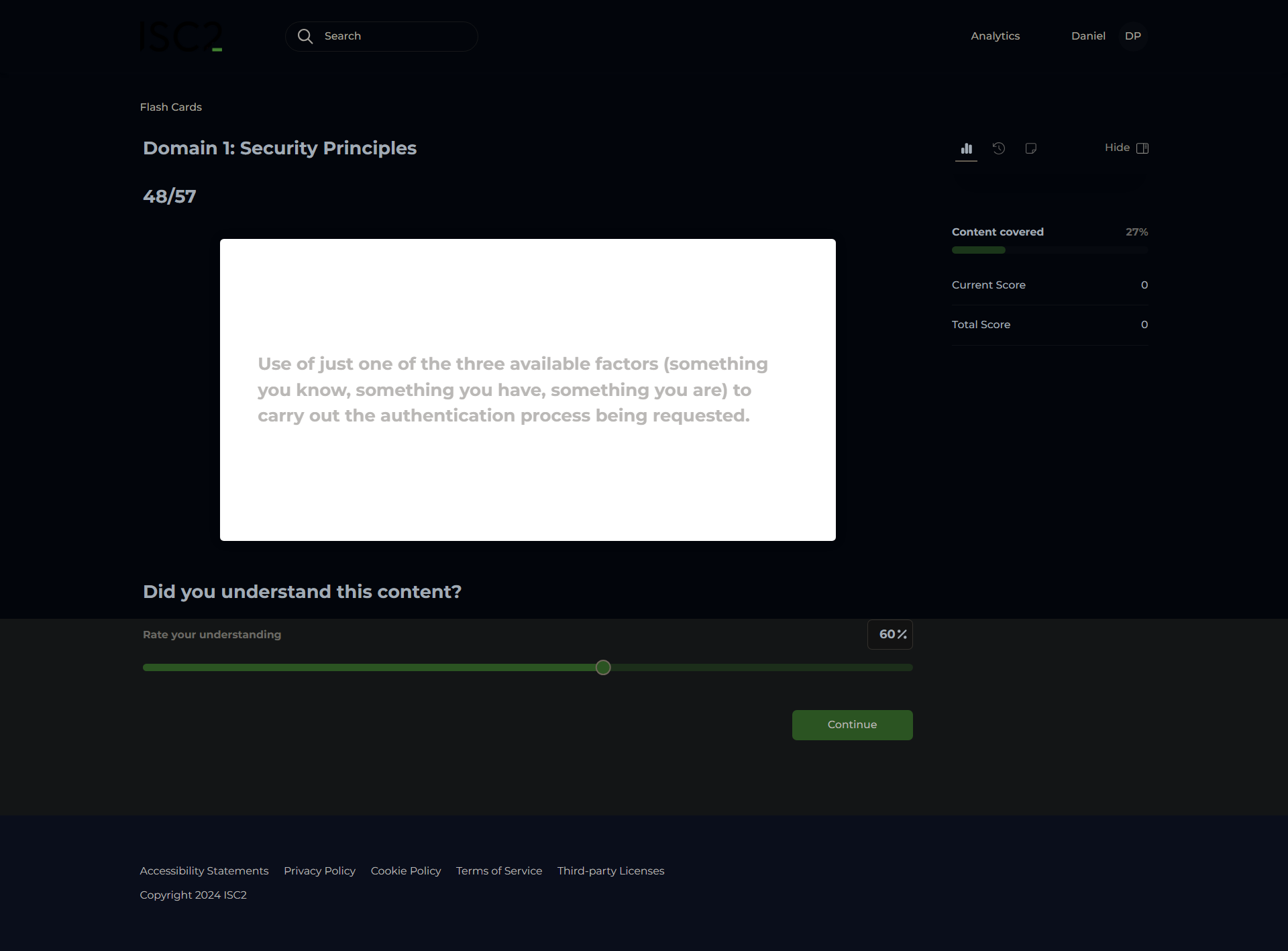
Single-Factor Authentication
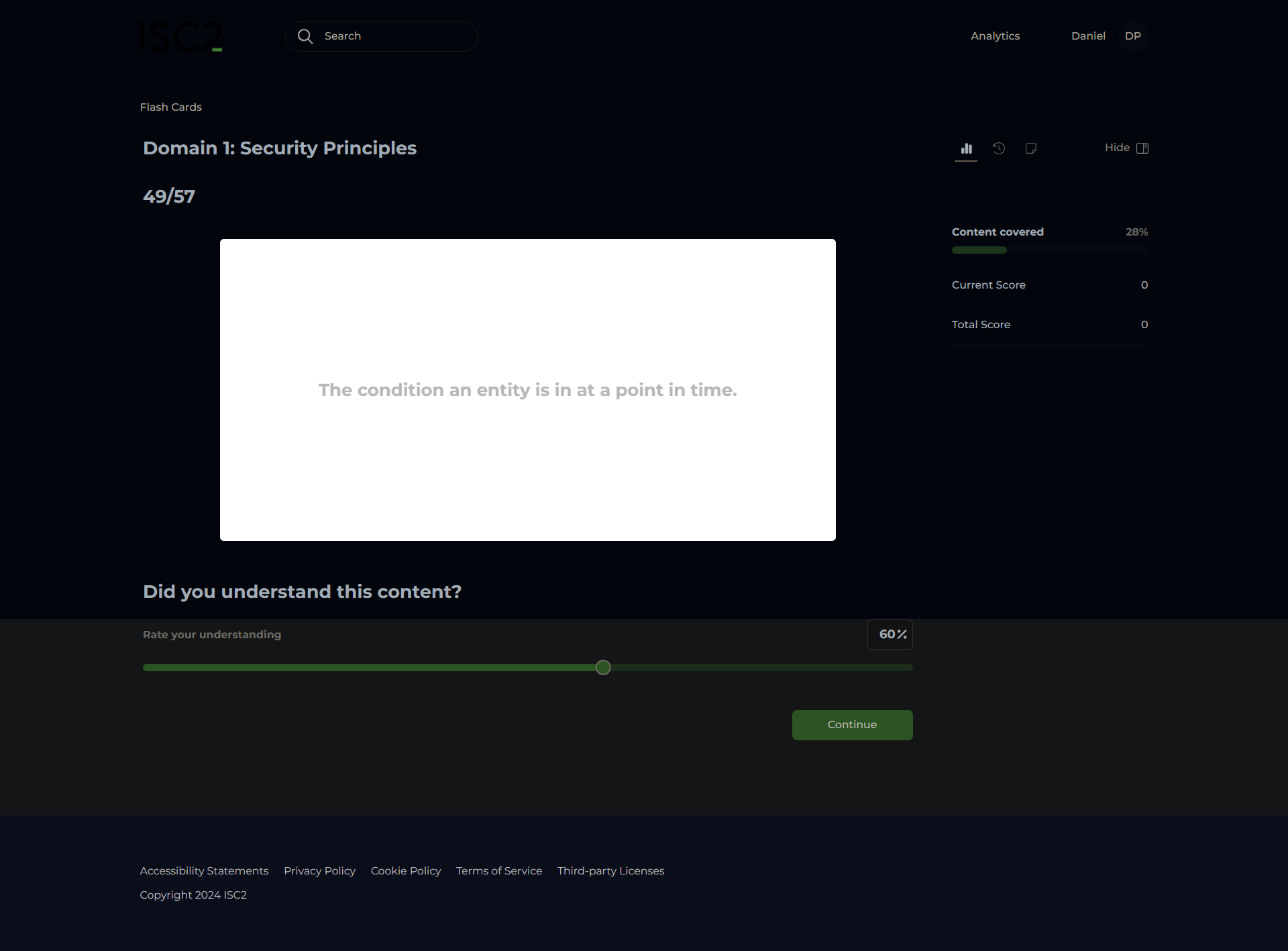
State
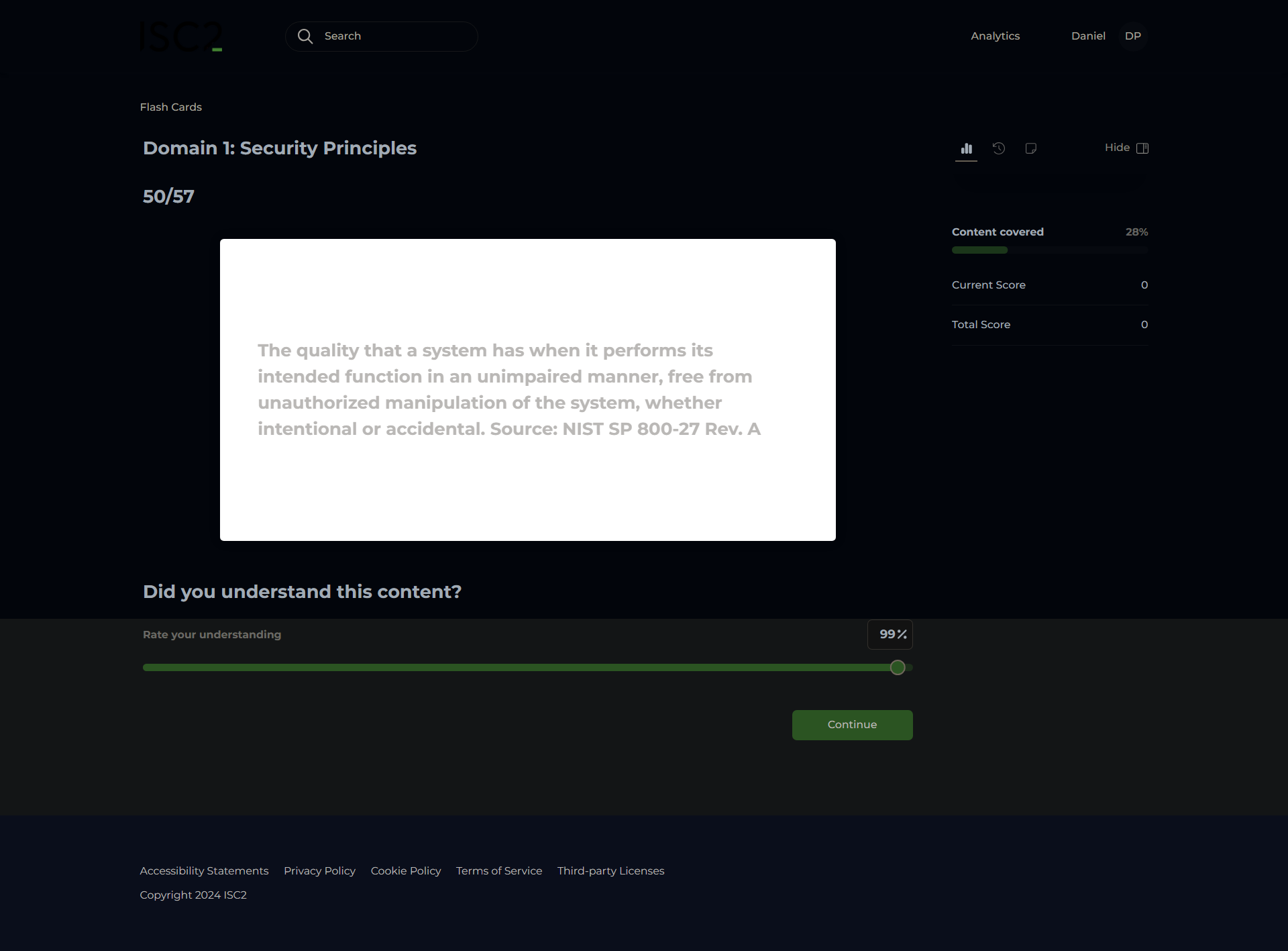
System Integrity
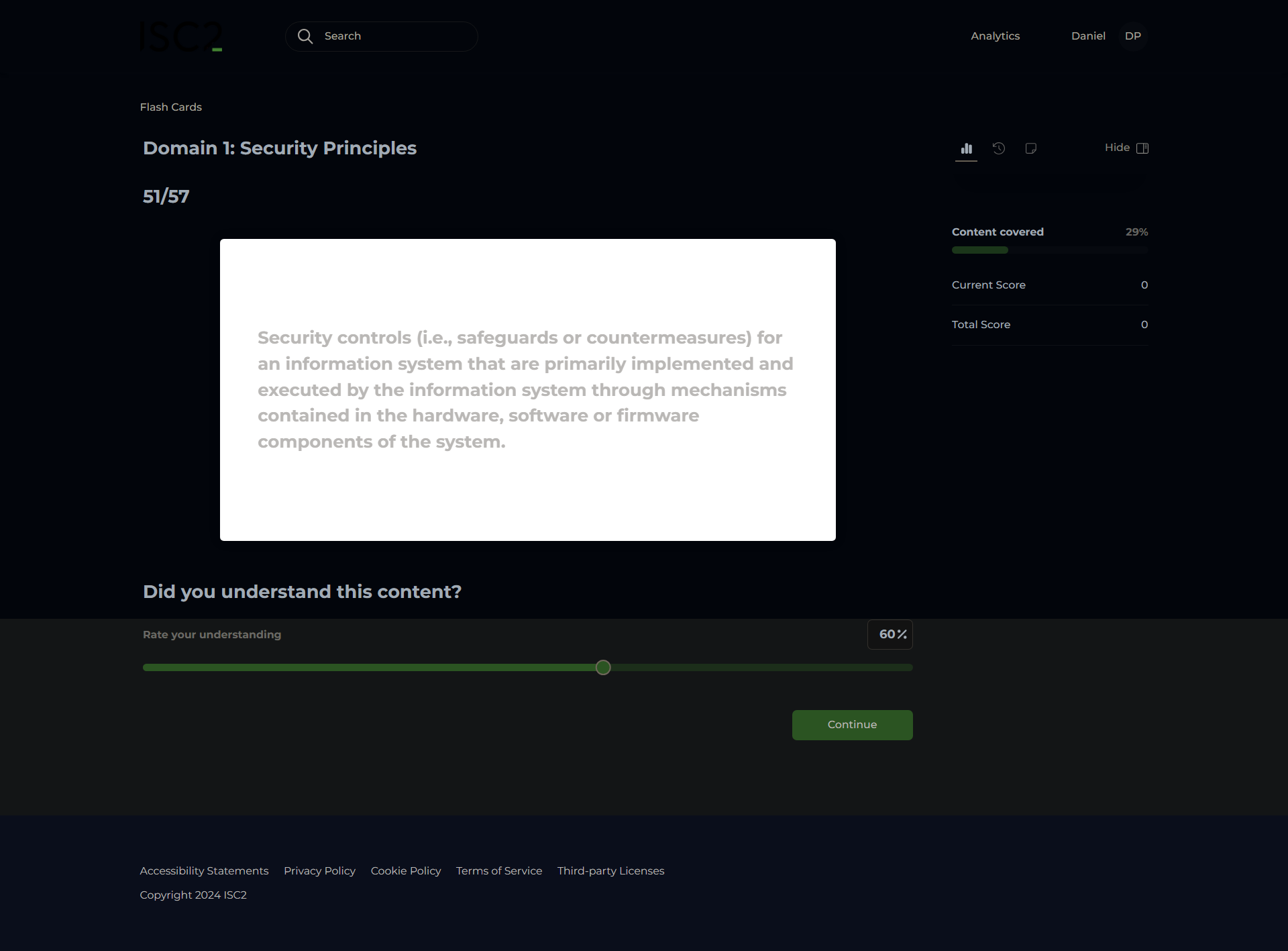
Technical Controls
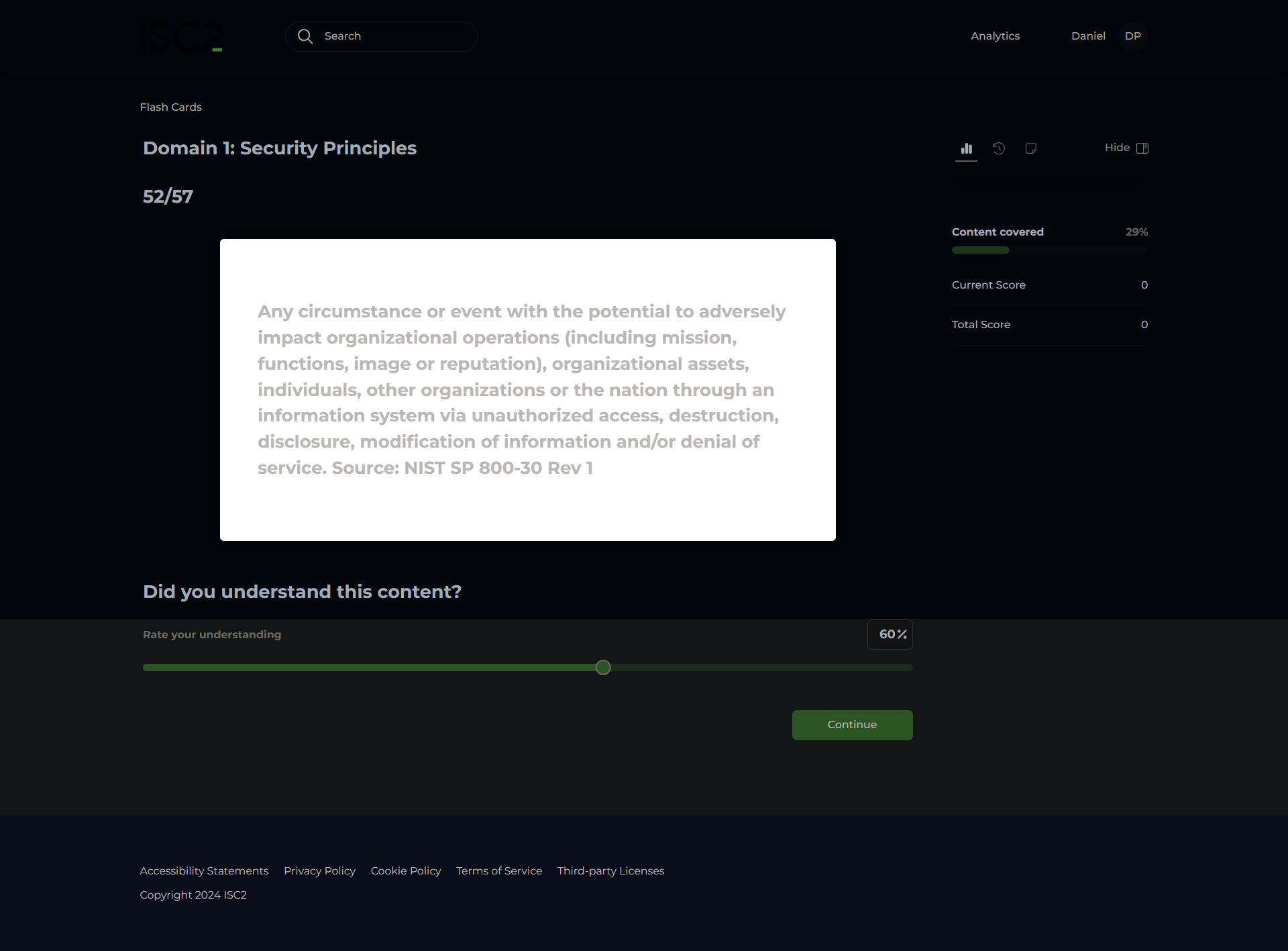
Threat
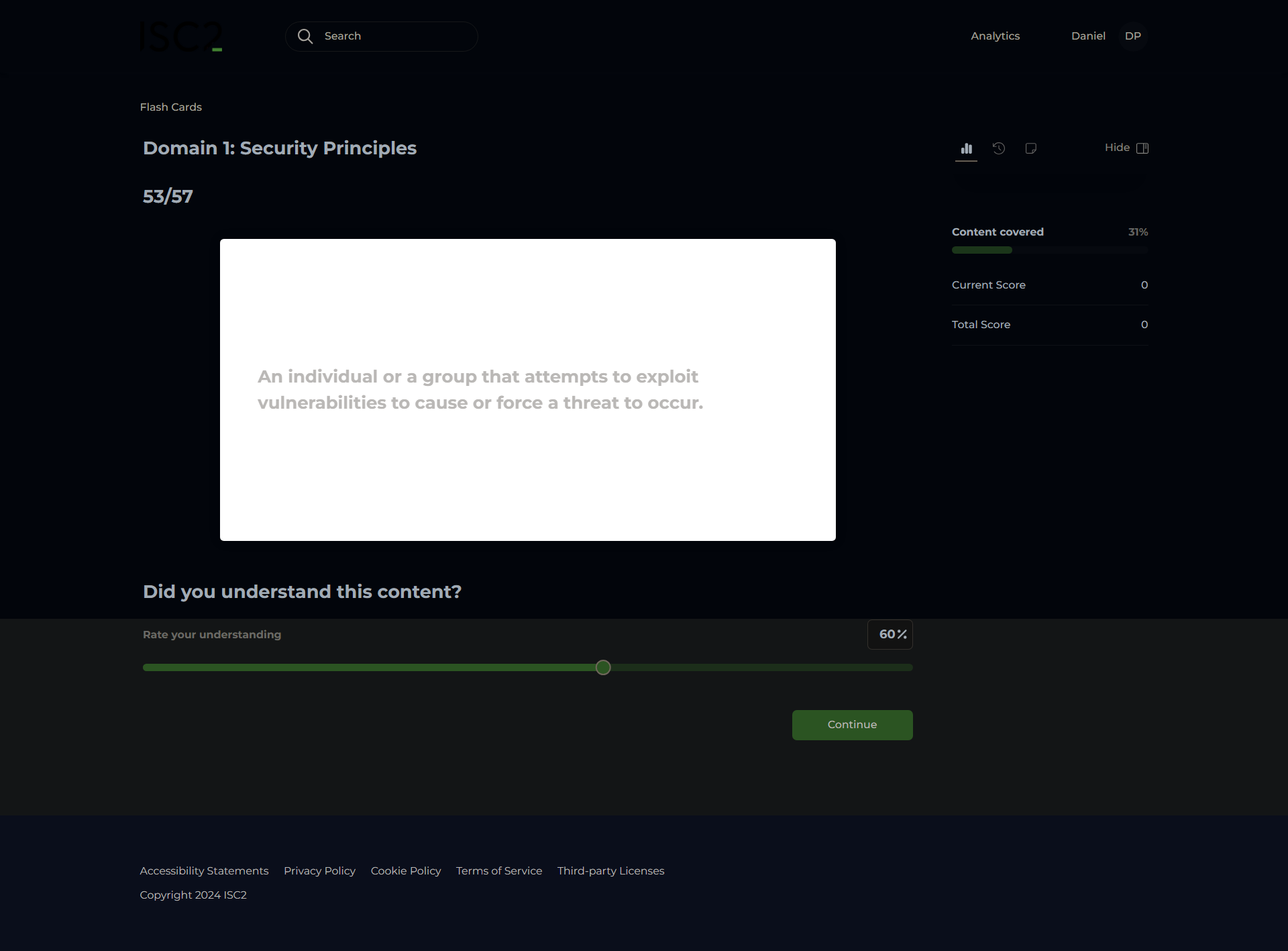
Threat Actor
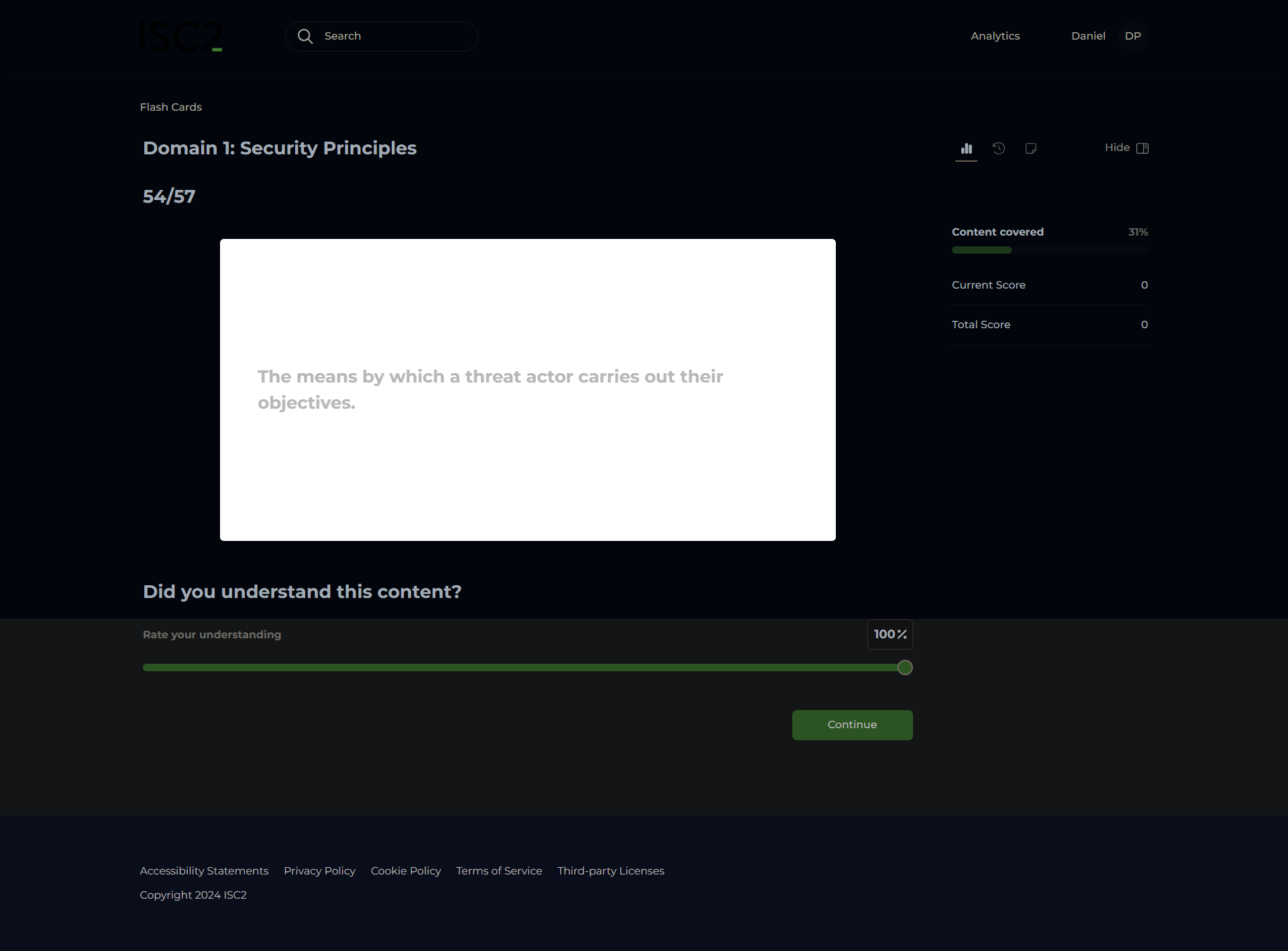
Threat Vector
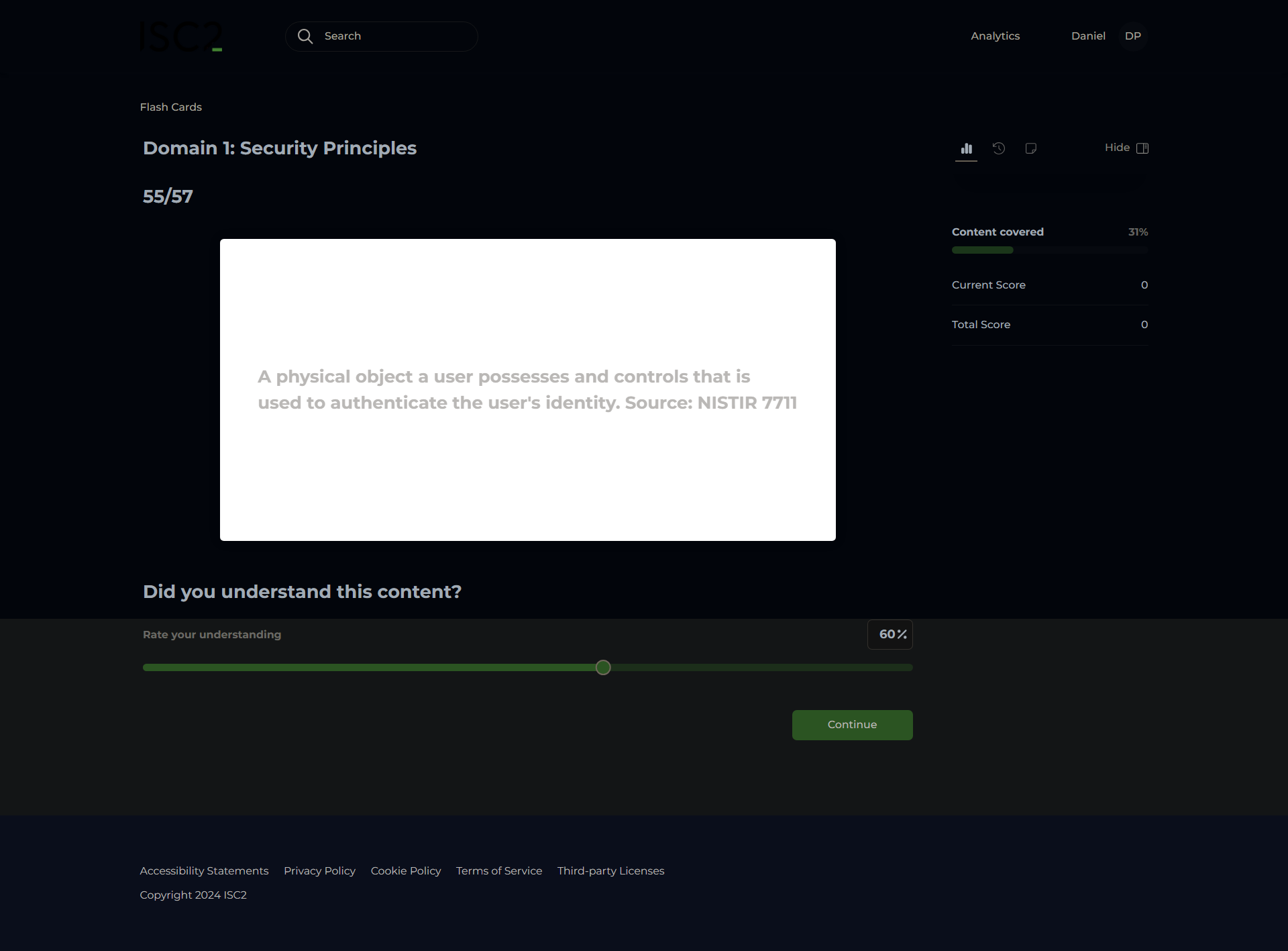
Token
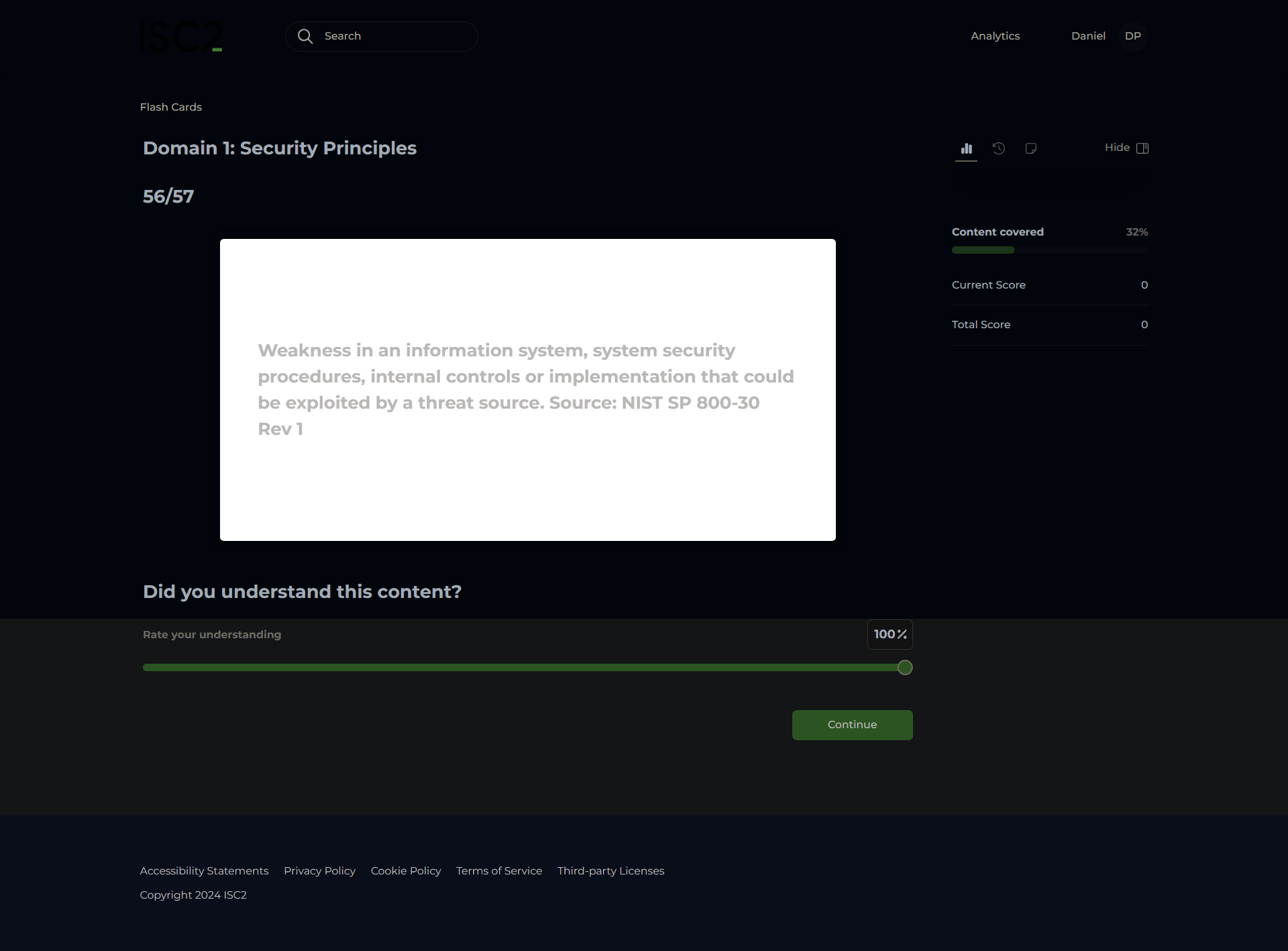
Vulnerability
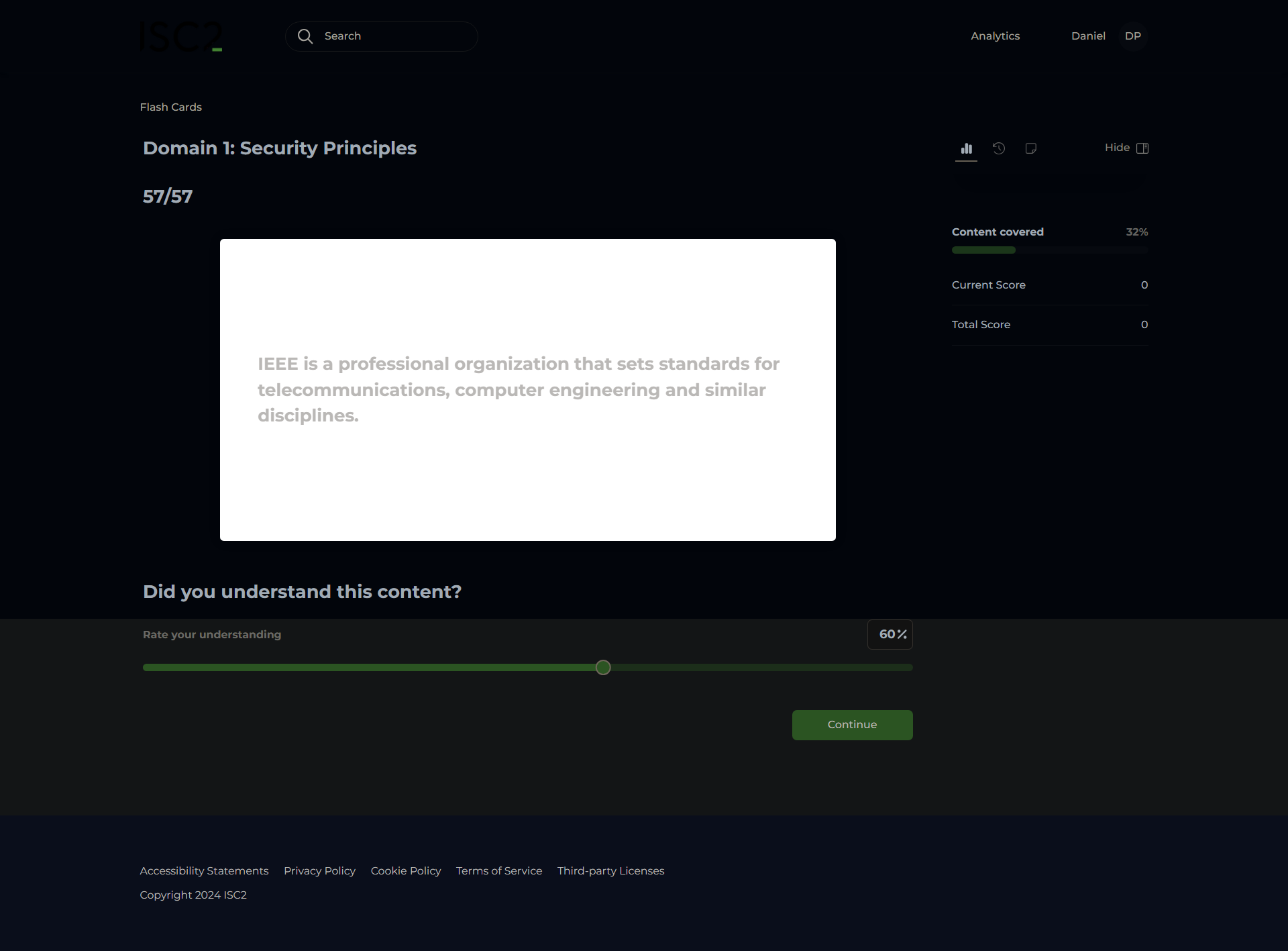
Institute of Electrical and Electronics Engineers